Sticky sessions or session affinity is a convenient strategy to keep subsequent requests always reaching the same pod.
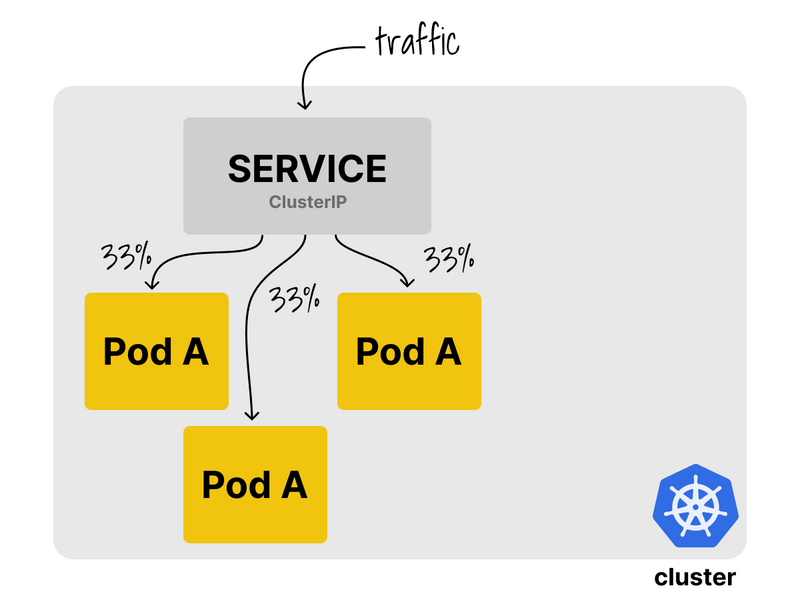
Let's look at how it works by deploying a sample application with three replicas and one service.
In this scenario, requests directed to the service are load-balanced amongst the available replicas.
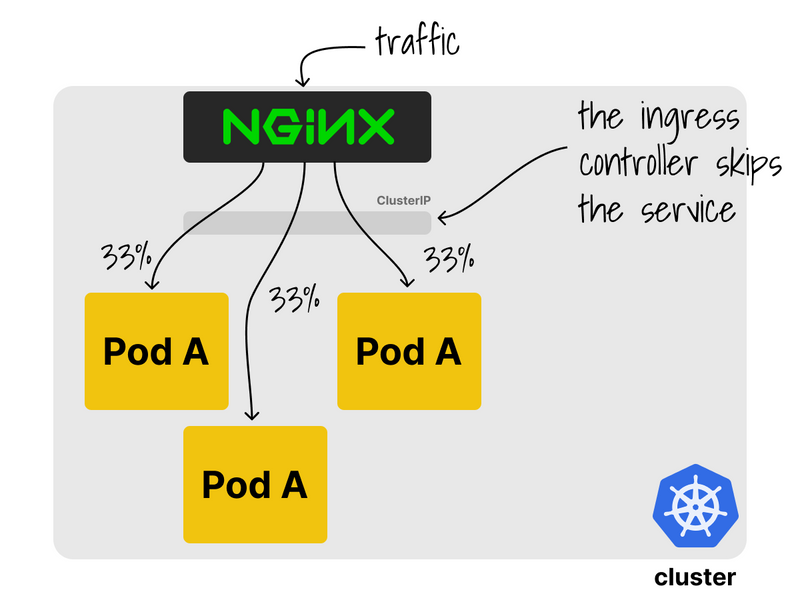
Let's deploy the ingress-nginx controller and create an Ingress manifest for the deployment.
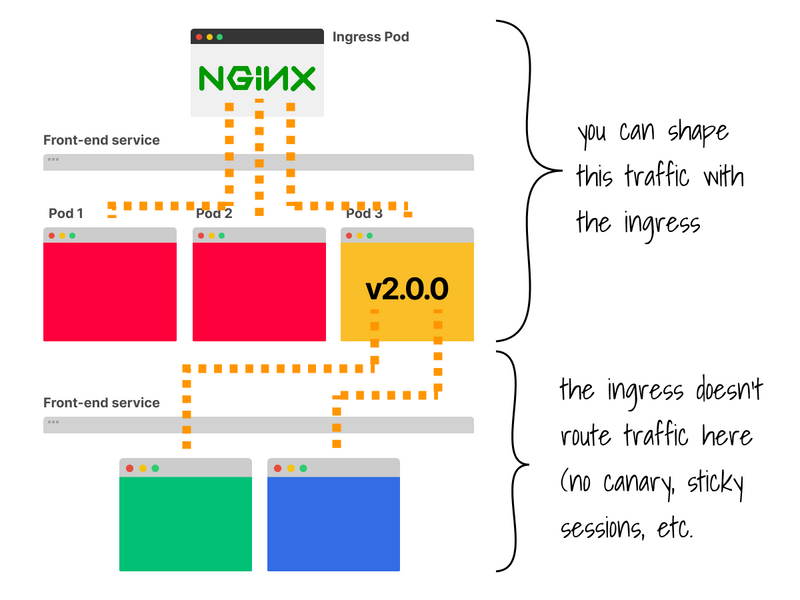
In this case, the ingress controller skips the services and load balances the traffic directly to the pods.
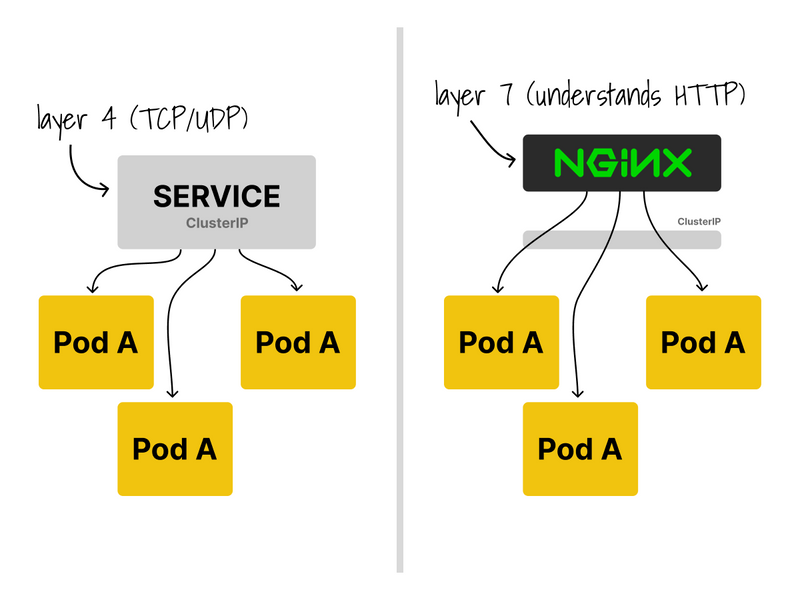
While the two scenarios end up with the same outcome (i.e. requests are distributed to all replicas), there's a subtle (but essential) distinction: the Service operates on L4 (TCP/UDP), whereas the Ingress is L7 (HTTP).
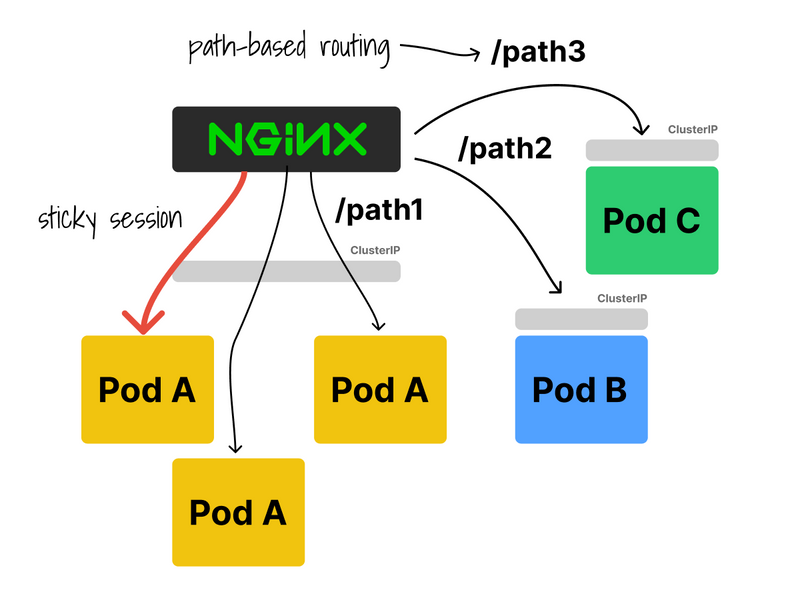
Unlike the service, the Ingress controller can route traffic based on paths, headers, etc.
You can also use it to define weights (e.g. 20-80 traffic split) or sticky sessions (all requests from the same origin always land on the same pod).
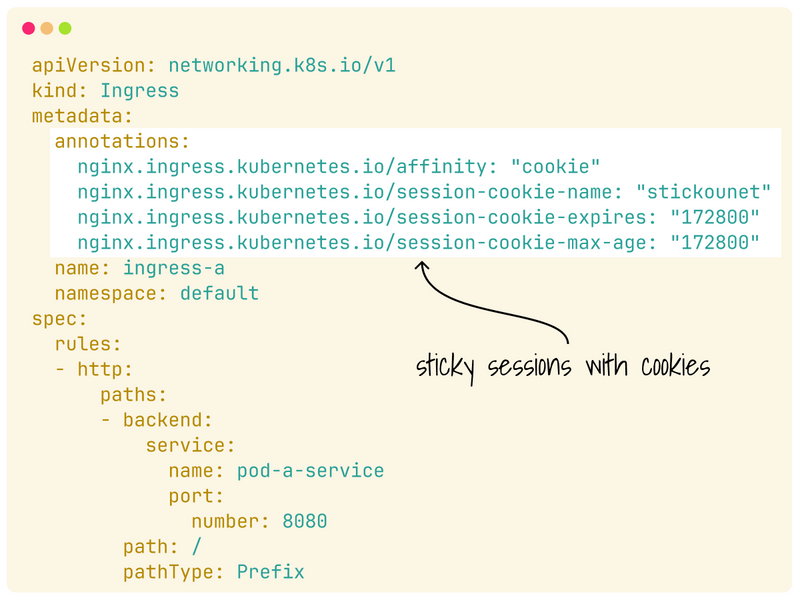
The following Ingress implements sticky sessions for the nginx-ingress controller.
The ingress writes a cookie on your browser to keep track of what instance you visited.
There are two convenient settings for affinity:
- balanced — requests are redistributed if the deployment scales up.
- persistent — no matter what, the requests always stick to the same pod.
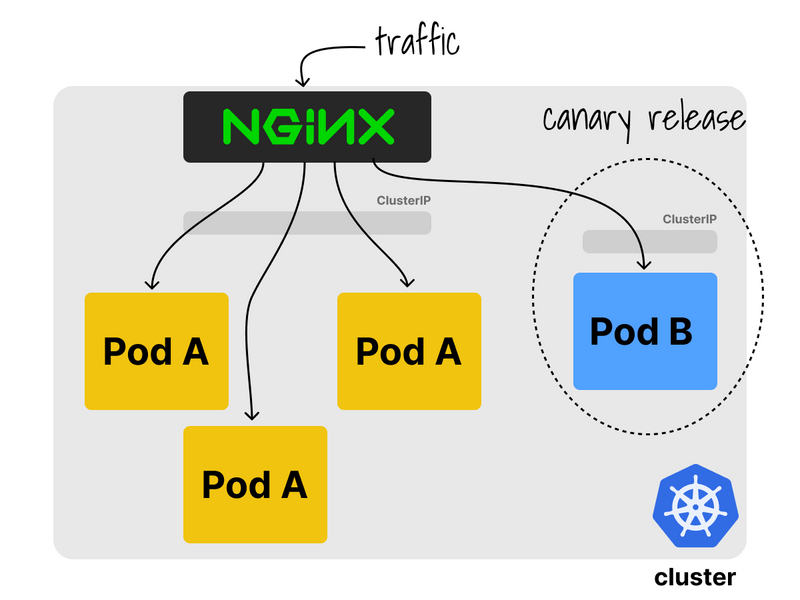
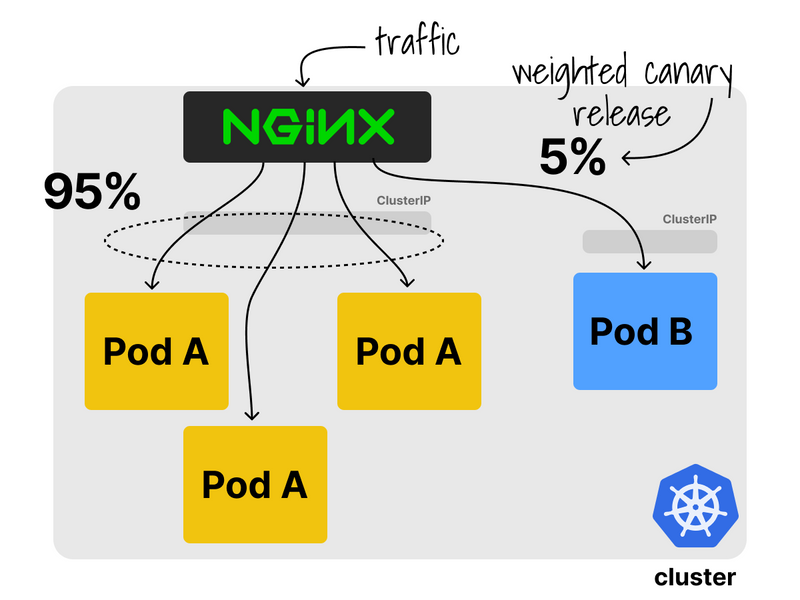
nginx-ingress can also be used for canary releases.
If you have two deployments and you wish to test a subset of the traffic for a newer version of that deployment, you can do so with a canary release (and impact a minimal amount of users).
In a canary release, each deployment has its own Ingress manifest.
However, one of those is labelled as a canary.
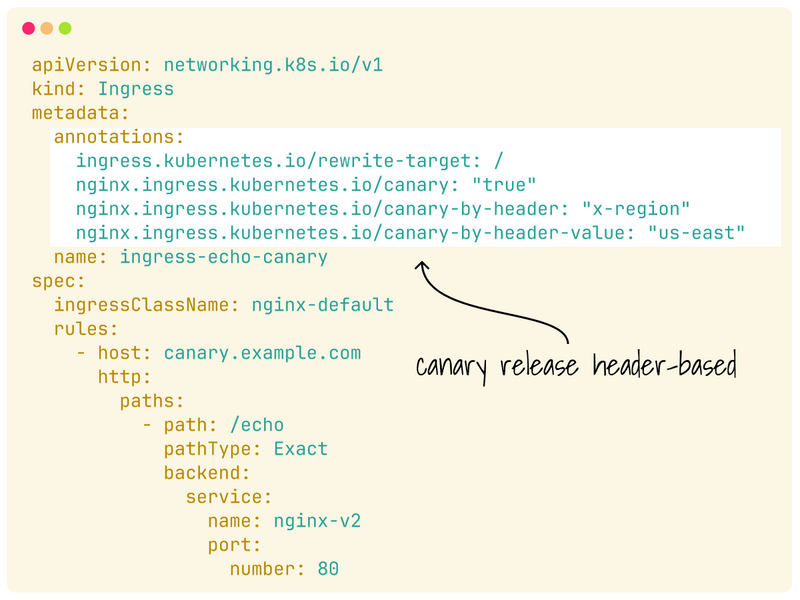
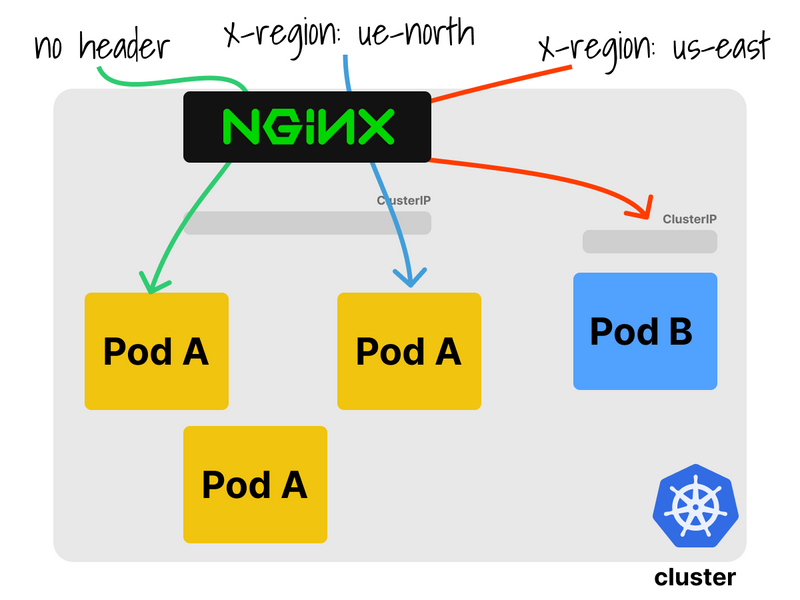
You can decide how the traffic is forwarded: for example, you could inspect a header or cookie.
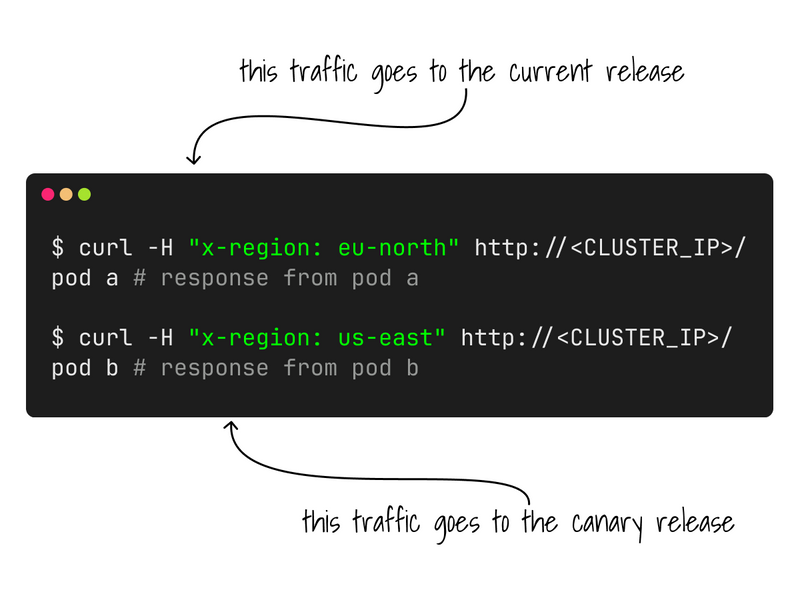
In this example, all traffic labelled east-us is routed to the canary deployment.
You can also decide which fraction of the total traffic is routed to the canary with weights.
But if the header is omitted in a subsequent request, the user will return to see the previous deployment.
How can you fix that?
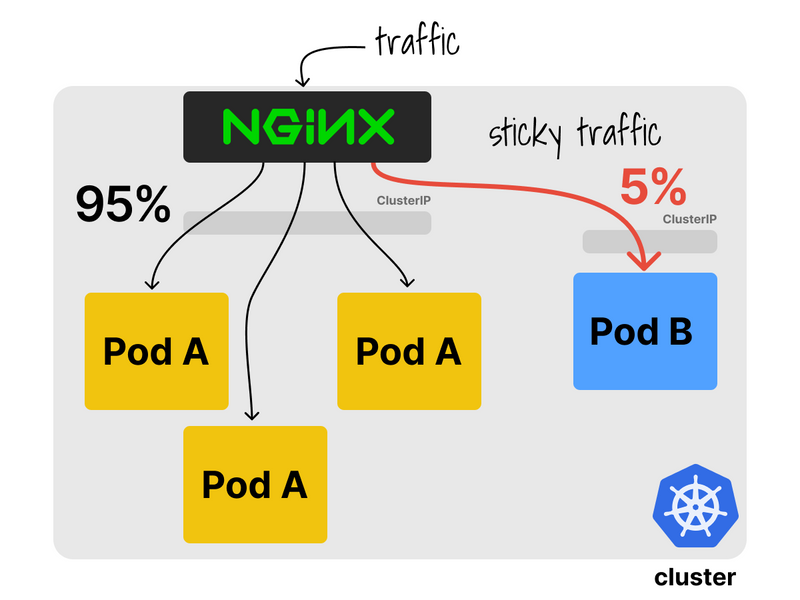
With sticky sessions!
You can combine canary releases and sticky sessions with ingress-nginx to progressively (and safely) roll out new deployments to your users.
It's important to remember that those types of canary releases are only possible for front-facing apps.
To roll out a canary release for internal microservices, you should look at alternatives (e.g. service mesh).
Is nginx-ingress the only option for sticky sessions and canary releases?
Not really, but the annotations might be different to other ingress controllers.
At Learnk8s, we've put together a spreadsheet to compare them.
And finally, if you've enjoyed this thread, you might also like:
- The Kubernetes workshops that we run at Learnk8s.
- This collection of past threads.
- The Kubernetes newsletter I publish every week.
While authoring this post, I also found the following resources valuable:



Top comments (13)
I would set a persistent session affinity in the ingress-nginx configuration to ensure users consistently land on the same pod. This way, even if headers or cookies are not sent, the traffic remains sticky to the initial pod. It prevents users from being redirected to different deployments after their first visit.
google baseball
Become an unbeatable racer in escape road – a high-speed chase game with vivid 3D graphics. Drive away from the police, collect coins, unlock supercars and prove your ultimate driving skills today!
As canary releases unfold, the infrastructure landscape reveals its colors, blending new harmonies into the existing tune. On the imagined Friday Night Funkin stage, each transition is a rap beat both challenging and exciting. Embrace this strategy boldly to gain an edge in your deployments.
Yes, on the other hand, canary releases allow you to test new features with a subset of users by routing a fraction of traffic to a new version of your application. By combining sticky sessions with canary releases, you can ensure that users who are routed to the canary deployment stay there for their session, providing a smoother experience while you test new features.
Miss Lewis.,Tapfit
I would set a persistent session affinity in the ingress-nginx configuration to ensure users consistently land on the same pod. This way, even if headers or cookies are not sent, the traffic remains sticky to the initial pod.
Poor Bunny
This can be either a fixed session or a compatible session. This article explains how it works in detail by deploying a sample application with three replicas and one service foodle.
This community offers practical, experience-based knowledge that companies can use to refine their products. Nitrile gloves may be doing well purble place online, but small changes can lead to even greater performance.
This session might be compatible or fixed. The visuals in Doodle Baseball are whimsical and charming, including vibrant animations and exaggerated gestures that animate each food-themed character.
Sticky sessions using cookies and weights in nginx-ingress caught my attention. I like how traffic routing can be managed so precisely. Image to Image AI
good explanation! Drive Mad is a free online challenge game where you navigate wild tracks filled with obstacles, driving carefully to complete all levels.