AWS re:Inforce is the Amazon Web Services annual event focused on security.
The event was led by Chris Betz, CISO of AWS.
During the keynote, Chris shared some of the insights that AWS embed security as part of their company's culture.
He talked about the Security Guardians program, a mechanism for distributing security ownership, and a culture of escalation – a process of making sure that the right people know about the problem at the right time.
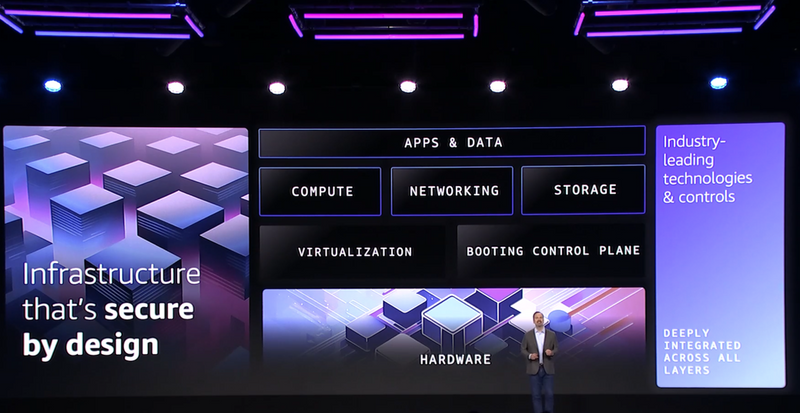
AWS infrastructure is secured by design at all layers – from hardware, virtualization, compute, networking, storage, and finally at the apps and data layer.
AWS Graviton4 was designed with built-in security features such as:
- Pointer authentication
- No simultaneous multi-threading (SMT)
- Full encryption of all high-speed physical interfaces
- Branch target identification
AWS Nitro System supports full isolation of customer's AI data from AWS operators:
- Encrypt sensitive AI data using keys that customers own and control
- Store data in a location of the customer's choice
- Securely transfer the encrypted data to the enclave for inferencing
- Encryption for ML accelerator, to Nitro, to the network, and back Reference:
- A secure approach to generative AI with AWS
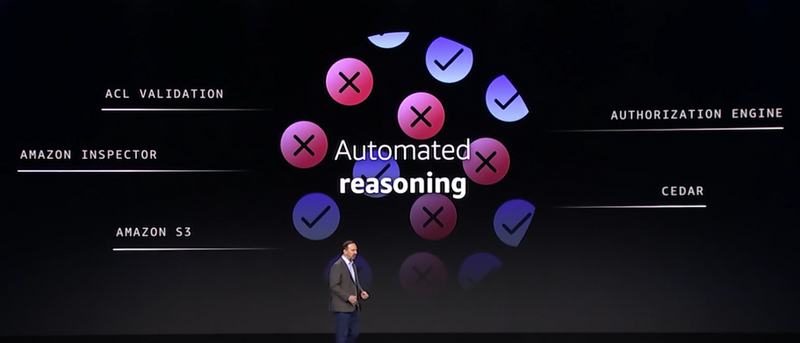
AWS is using Automated Reasoning for multiple purposes, such as:
- Verify the correctness of cryptographic protocols, authorization logic, and consistency of storage systems (such as Amazon S3 ShardStore)
- Verify security mechanisms such as firewalls, detection, and coding practices
- A strong identity and access management
- Hybrid environments
- Complex network segmentation
- Expanding application landscape and workforce mobility
Announcement - AWS Private CA Connector for SCEP (Currently in Preview)
Simple Certificate Enrollment Protocol (SCEP), lets you use a managed and secure cloud certificate authority (CA) to enroll mobile devices securely and at scale.
References:
- AWS Private CA introduces Connector for SCEP for mobile devices (Preview)
- AWS Private CA Connector for SCEP documentation
Announcement - Passkeys as 2nd Factor Authenticators in AWS IAM
AWS now allows customers the options for strong authentication by launching support for FIDO2 passkeys as a method for multi-factor authentication (MFA) as we expand our MFA capabilities. Passkeys deliver a highly secure, user-friendly option to enable MFA for many of our customers.
References:
- AWS Identity and Access Management now supports passkey as a second authentication factor
- AWS adds passkey multi-factor authentication (MFA) for root and IAM users
- Passkeys enhance security and usability as AWS expands MFA requirements
Announcement - IAM Access Analyzer unused access findings recommendation (Currently in Preview)
AWS IAM Access Analyzer provides tools to set, verify, and refine permissions. With the new announcement, IAM Access Analyzer offers actionable recommendations to guide you to remediate unused access.
References:
- AWS IAM Access Analyzer now offers recommendations to refine unused access
- IAM Access Analyzer updates: Find unused access, check policies before deployment
- IAM Access Analyzer - Unused access findings
Announcement - Malware Protection for S3 Amazon GuardDuty
Amazon GuardDuty is a threat detection service that continuously monitors, analyzes, and processes specific AWS data sources and logs in the AWS environment. This expansion of GuardDuty Malware Protection allows scanning newly uploaded objects to Amazon S3 buckets for potential malware, viruses, and other suspicious uploads and taking action to isolate them before they are ingested into downstream processes.
References:
- Detect malware in new object uploads to Amazon S3 with Amazon GuardDuty
- Introducing Amazon GuardDuty Malware Protection for Amazon S3
- GuardDuty Malware Protection for S3
AWS Generative AI stack and built-in security controls:
- Amazon Q - Tools and services to write secure and robust code (Amazon Q Developer, Amazon Q Business)
- Amazon Bedrock - Helps keep data secure and private. All data is encrypted in transit and at rest. Data used for customization is securely transferred through the customer's VPC
- AWS Nitro System - Allows customers to secure AI infrastructure includes zero trust access to sensitive AI data
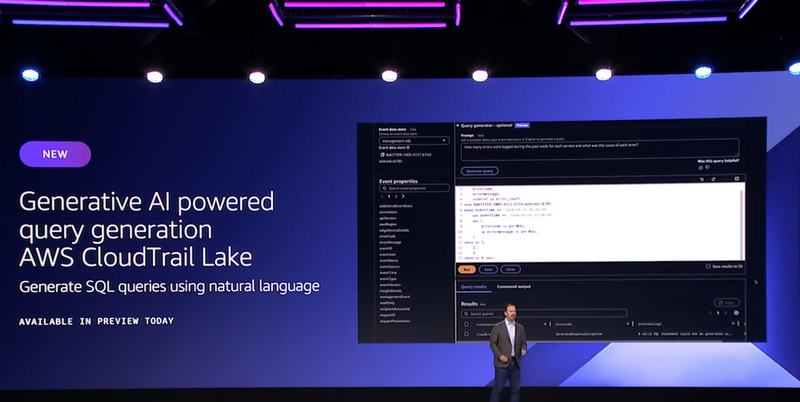
Announcement - Generative AI-powered query generation AWS CloudTrail Lake (Currently in Preview)
AWS CloudTrail Lake lets customers run SQL-based queries on your events. This new feature empowers users who are not experts in writing SQL queries or who do not have a deep understanding of CloudTrail events.
References:
- AWS CloudTrail Lake announces AI-powered natural language query generation (preview)
- Simplify AWS CloudTrail log analysis with natural language query generation in CloudTrail Lake (preview)
- Create CloudTrail Lake queries from English language prompts
Steve Schmidt, the Chief Security Officer of Amazon, shared some of the experiences Amazon has had using generative AI.
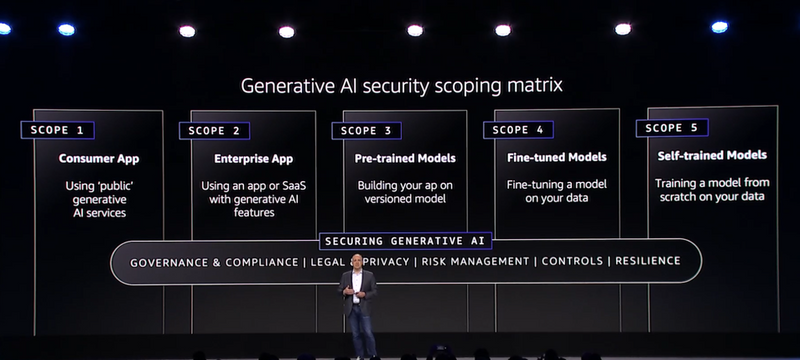
Generative AI security scoping matrix:
- Consumer App - Using "public" generative AI services
- Enterprise App - Using an app or SaaS with generative AI features
- Pre-trained models - Building an app on a versioned model
- Fine-tuned models - Fine-tuning a model based on customer's data
- Self-trained models - Training a model from scratch, based on the customer's data References:
- An Introduction to the Generative AI Security Scoping Matrix
- Securing generative AI: Applying relevant security controls
Handling service data properly:
- Know what you have, where is it, how it is stored, who has access for what purposes, and how that data is used over time
- Trust boundaries for retrieval-augmented generation (RAG)
- Continued testing
- Security guardrails (such as GuardRails for Amazon Bedrock)
The full keynote is available at: https://www.youtube.com/watch?v=skH3Q90llss
About the Author
Eyal Estrin is a cloud and information security architect, and the author of the books Cloud Security Handbook, and Security for Cloud Native Applications, with more than 20 years in the IT industry.
You can connect with him on Twitter.
Opinions are his own and not the views of his employer.
👇Help to support my authoring👇
☕Buy me a coffee☕








Top comments (1)
AWS re:Inforce 2024 had some awesome updates. They shared new tools to help keep data secure, which is great to see as they improve cloud safety.