The term MCP (Model Context Protocol) was first introduced by Anthropic in November 2024 as an open standard and open-source framework. MCP standardizes how AI systems like large language models integrate and share data with external tools and data sources.
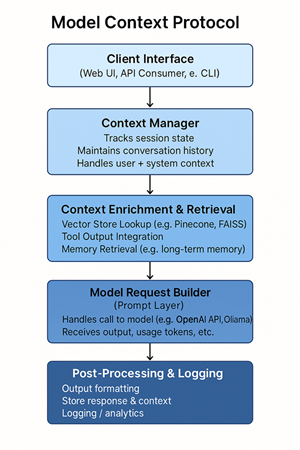
Below is a common MCP flow:
MCPs offer easy integration to consume data and take actions; however, it was not built with security in mind.
In this blog post, I will share some of the most common security risks related to MCPs and provide recommendations for mitigating some of the common risks.
Common security risks using MCP
Below is a list of common security risks relating to the deployment and use of MCP servers:
- Lack of default authentication: Many current MCP implementations lack built-in authentication, increasing exposure to unauthorized access.
- Token theft: MCP servers may store sensitive tokens (e.g., OAuth tokens) insecurely, risking exposure if the server is compromised.
- Prompt injection attacks: Attackers inject hidden or malicious instructions into tool descriptions or inputs that AI models might execute unintentionally.
- Privilege escalation via AI agents: Attackers can manipulate AI agents to gain unauthorized access or perform unauthorized actions due to over-privileged permissions or weak authentication.
- Command injection vulnerabilities: Poor input validation in MCP servers can allow remote command execution attacks, compromising systems.
- Supply chain attacks: Malicious MCP packages or dependencies can be introduced during build or distribution, allowing attackers to deliver harmful payloads or compromise systems without user knowledge.
- Untrusted MCP sources: Connecting to MCP servers or tools from unknown or unvetted sources may lead to data exfiltration, hidden malicious commands, or unauthorized access since MCP servers execute code and have access to sensitive data.
- Lack of observability: Insufficient monitoring and logging of MCP interactions and tool usage obscures detection of malicious activities or anomalies, enabling attackers to act undetected within MCP workflows.
- No approval workflows: Absence of human-in-the-loop or explicit approval mechanisms for MCP-executed actions allows AI agents to perform unauthorized or harmful operations without oversight or consent.
Recommendations for securing MCP servers
Now that we have introduced the most common security risks related to MCP servers, let us deep dive into potential mitigation controls:
Identity and Access Management
Implementing robust authentication controls is critical for the security of the Model Context Protocol (MCP), which acts as a universal bridge for AI models to securely interact with external data, APIs, and services.
- Use OAuth 2.1 as a standard authentication mechanism to access MCP servers.
AWS - Guidance for Deploying Model Context Protocol Servers on AWS
Azure - Smart AI Integration with the Model Context Protocol (MCP)
GCP - Using OAuth 2.0 to Access Google APIs
- For MCP clients, request access tokens via OAuth 2.1 authorization code flow with PKCE.
AWS - Using PKCE in authorization code grants
Azure - Microsoft identity platform and OAuth 2.0 authorization code flow
GCP – Authorization resources – best practices
- Use IAM roles to grant least privilege and temporary access to MCP servers.
AWS - Security best practices in IAM
Azure - Enhance security with the principle of least privilege
GCP - Use IAM securely
- Configure conditional access policies based on user risk profile, network, device, or application context (e.g., IP, geo-location, device compliance).
AWS - Using attributes for access control
Azure - Developer guide to Conditional Access authentication context
GCP - Overview of IAM Conditions
- Implement MFA for any interactive login to MCP servers.
AWS - Adding MFA to a user pool
Azure - Secure user sign-in events with Microsoft Entra multifactor authentication
GCP – Multi-factor authentication requirement for Google Cloud
Secure credentials and token management
Secure secrets management is essential in the Model Context Protocol to safeguard sensitive credentials by avoiding hardcoding and using trusted storage, strict access controls, and frequent rotation.
- Never hardcode secrets (API keys, tokens, passwords) in source code or commit them to version control.
- Securely store service account and API credentials using secret management systems.
- Limit secret access to only the required MCP components or services. Leverage role-based access control (RBAC) to restrict who/what can retrieve secrets. Use short-lived, scoped credentials where possible instead of long-lived static secrets.
- Regularly rotate static secrets and refresh tokens to minimize exposure duration.
- Mask secrets in logs and avoid exposing them during debugging or error reporting.
- Monitor access to secrets using cloud provider audit logs and alerts. Detect unusual access patterns or potential leaks early for a timely response.
- Separate secrets for development, staging, and production environments. Also, isolate secrets accessed by different MCP servers or services to limit risk and simplify management.
AWS - AWS Secrets Manager best practices
Azure - Best practices for secrets management in Key Vault
GCP - Secret Manager best practices
Encryption in Transit
Encrypting data in transit is essential for Model Context Protocol implementations to protect information from interception and tampering, ensuring secure communication channels between AI models, clients, and services.
- Use Transport Layer Security (TLS) to encrypt data in transit between MCP clients and servers. Use strong TLS versions (TLS 1.2 or 1.3) and disable outdated protocols.
- MCP API endpoints should be accessible only via HTTPS, ensuring that all HTTP traffic is automatically encrypted.
- Ensure clients validate server certificates rigorously, including checking certificate chains, expiration, and revocation status.
- For stronger authentication and encryption during transport, consider mutual TLS where both client and server present certificates.
AWS - TLS 1.2 to become the minimum TLS protocol level for all AWS API endpoints
Azure - Recommendations for data encryption
GCP - SSL policies for SSL and TLS protocols
Securing network access to MCP servers
Limiting access to the MCP server allows decreasing the attack surface (from both internal and external networks) and lowers the chance of unauthorized access.
- Deploy MCP servers with strict network access policies, ensuring only necessary ports are open.
AWS - Control traffic to your AWS resources using security groups
Azure - How network security groups filter network traffic
GCP - VPC firewall rules
- Allow access only to trusted entities; avoid exposing MCP endpoints publicly unless necessary.
AWS - Connect your VPC to services using AWS PrivateLink
Azure - What is the Azure Private Link service?
GCP - Overview of VPC Service Controls
- Employ Web Application Firewalls (WAFs) to mitigate common web attacks.
AWS - How to manage AI Bots with AWS WAF and enhance security
Azure - Protect Azure OpenAI using Azure Web Application Firewall on Azure Front Door
GCP - Integrating Cloud Armor with other Google products
Harden Input Validation and Prevent Injection Attacks
Hardened input validation is essential in MCP security to ensure that all incoming data is rigorously checked and sanitized, preventing injection attacks that could compromise model integrity or trigger unauthorized behaviors.
- Enforce comprehensive schema validation with length, range, and type constraints; reject unknown or unexpected fields to prevent parameter pollution and injection.
- Normalize and escape inputs appropriately based on their usage context to mitigate injection vectors like command, code, or HTML injection.
- Inspect and sanitize outputs to remove sensitive or potentially malicious content before returning data to clients or models. Use pattern matching and data loss prevention tools to prevent unintended data leakage.
- Implement strict allow-lists for inputs, outputs, and tool actions, denying all non-explicitly permitted operations to reduce attack surfaces.
References:
Enterprise-Grade Security for the Model Context Protocol (MCP): Frameworks and Mitigation Strategies
AWS - Safeguard your generative AI workloads from prompt injections
Azure - Prompt Shields
GCP - Overview of prompting strategies
Supply Chain / SBOM
Supply chain risks in MCP arise from the integration of unvetted or open-source MCP implementations, which can introduce malicious code or vulnerabilities that compromise the security and integrity of AI workflows and connected systems.
- Only use MCP implementations and components from trusted, well-maintained sources to reduce risks of malicious code or vulnerabilities.
AWS - Automated scan types in Amazon Inspector
Azure - Vulnerability assessments for supported environments
GCP - Artifact analysis and vulnerability scanning
- Implement artifact signing and integrity verification to ensure MCP binaries, containers, and dependencies are authentic and untampered.
AWS - What is AWS Signer?
Azure - What is Trusted Signing?
GCP - Binary Authorization overview
- Maintain a detailed Software Bill of Materials (SBOM) to track all MCP-related components and dependencies, aiding in vulnerability management and compliance.
AWS - Amazon Inspector SBOM Generator
Azure - Microsoft opens sources its software bill of materials (SBOM) generation tool
GCP - Generate and store SBOMs
Rate Limit / DoS protection
Rate limiting and DoS protection are critical for MCP servers to prevent abuse by controlling the frequency of requests and mitigating potential denial-of-service attacks that could degrade service availability or exhaust system resources.
- Use intelligent throttling that adapts limits based on request context, user roles, and endpoint complexity to prevent abuse without overly restricting legitimate use.
AWS - Throttle requests to your REST APIs for better throughput in API Gateway
Azure - Advanced request throttling with Azure API Management
GCP - Rate-limiting
- Set strict limits on request frequency for individual users or API keys, reducing the risk of resource exhaustion or abusive behaviors.
- Continuously audit request patterns, limit violations, and traffic anomalies for early detection and tuning.
- Use DDoS protection services to defend against volumetric attacks alongside rate limiting.
OWASP - Denial of Service Cheat Sheet
AWS - Applying rate limiting to requests in AWS WAF
Azure - What is rate limiting for Azure Front Door?
GCP - Rate limiting overview
- Analyze usage and performance data periodically to fine-tune thresholds, avoiding false positives or overly restrictive policies.
Enhancing Security and Oversight in MCP Operations
"Human-in-the-loop" is essential for MCP security because it introduces a mandatory human oversight step for sensitive or high-risk actions initiated by the AI, preventing unchecked or malicious behavior by requiring explicit user confirmation before executing critical operations.
- Mandate human approval for actions with financial, security, or reputational impact before the MCP server executes them, preventing unauthorized or malicious commands from running automatically.
- Provide users with clear visibility into AI tool actions, such as showing active tool usage or pending approvals, enabling timely intervention if suspicious or unintended behaviors occur.
- Automatically flag high-risk tool calls or data outputs (e.g., file writes, external communications, large sensitive data transfers) for human review as part of the workflow.
- Ensure that only authorized users can approve sensitive actions, leveraging fine-grained OAuth scopes and role-based access controls.
- Maintain detailed records of prompts, user decisions, and tool invocations to enable security audits, forensic investigations, and compliance reporting.
- Educate stakeholders on when and why human oversight is necessary in MCP workflows, reinforcing their role in preventing AI-driven security risks.
AWS - Building Generative AI prompt chaining workflows with human in the loop
Azure - Build AI Agents in Azure Logic Apps
GCP - Create a human-in-the-loop workflow using callbacks
Establish Comprehensive Observability and Incident Response
Establishing comprehensive observability and incident response capabilities is crucial for MCP security, as it enables continuous monitoring, rapid detection, and effective remediation of suspicious activities and failures within complex AI-driven interactions.
- Log every MCP interaction, including who or what invoked a tool, the parameters used, and the resulting outputs, ensuring logs are tamper-proof and securely stored for auditability and forensic analysis.
AWS - Generative AI observability
Azure - Observability in generative AI
GCP - Model monitoring metrics
- Integrate MCP logs into centralized Security Information and Event Management (SIEM) systems to correlate MCP events with broader infrastructure telemetry for real-time detection of anomalies or suspicious patterns.
AWS - Protecting AI workloads with GuardDuty
Azure - Overview - AI threat protection
GCP - Model Armor integration with Vertex AI
- Set up alerts for abnormal MCP behavior, such as unexpected tool usage, excessive frequency of calls, or privilege escalations, leveraging cloud-native monitoring tools to enable rapid incident detection and response.
- Define clear procedures for MCP-related security events, including containment, root cause analysis, mitigation, and post-incident reviews, incorporating automated response where feasible to reduce mean time to recovery.
Summary
In this blog post, I have reviewed common risks related to the use of MCP servers and provided recommendations for mitigating those risks, while using references from the hyper-scale cloud providers' documentation.
As technology evolves, we should expect to see more threats, and we need to keep up with technology trends, go back to our deployments, and strengthen the implemented controls.
About the author
Eyal Estrin is a cloud and information security architect, an AWS Community Builder, and the author of the books Cloud Security Handbook and Security for Cloud Native Applications, with more than 25 years in the IT industry.
You can connect with him on social media (https://linktr.ee/eyalestrin).
Opinions are his own and not the views of his employer.



Top comments (3)
Hi,
When people talk about securing MCP servers, I always think about it in layers rather than a single solution. Strong access control, constant monitoring, and preparing for unexpected attack vectors matter just as much as firewalls. Interestingly, that same mindset applies in strategy-based games where defense is the core mechanic. In games like Haunted Dorm, you survive by upgrading doors, managing resources wisely, and anticipating enemy behavior, which feels surprisingly similar to hardening a server environment. If anyone enjoys seeing defense concepts played out in a fun way, this page explains that game dynamic pretty well: haunteddormapks.com
Securing MCP servers is such an important topic, especially with how fast cyber threats evolve these days. I like how the focus isn’t just on the technical safeguards but also on creating a mindset of proactive security—because one weak point can expose so much. It actually reminds me of how Roja Directa ensures reliable access to streams; just like servers need strong protection, platforms need stability so users can trust them without worrying about interruptions. Do you think most organizations invest enough in preventive measures, or do they usually wait until after a breach happens?
This is such a well-explained breakdown of the challenges with modern authorization systems especially when scaling. It’s fascinating how similar the concept is in mobile gaming too, like in CPM2 Pro . Games often struggle with permission layers for unlocking premium versions or all cars. The latest versions are doing a better job with smoother access flows, just like in the dev world.
Some comments may only be visible to logged-in visitors. Sign in to view all comments.