When talking about the public cloud, I always like the analogy to the OSI model.
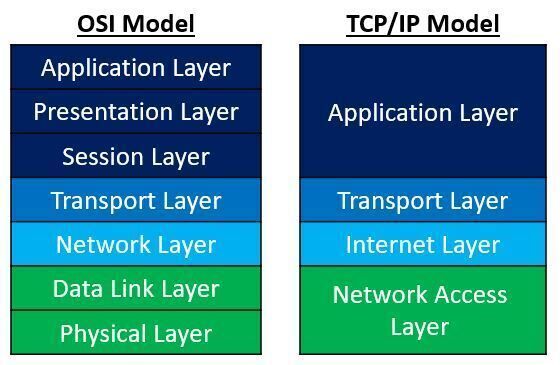
"The Open Systems Interconnection model (OSI model) is a conceptual model. Communications between a computing system are split into seven different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and Application" (Wikipedia)
A similar and shorter model of the OSI model is the TCP/IP model.
Here is a comparison of the two models:
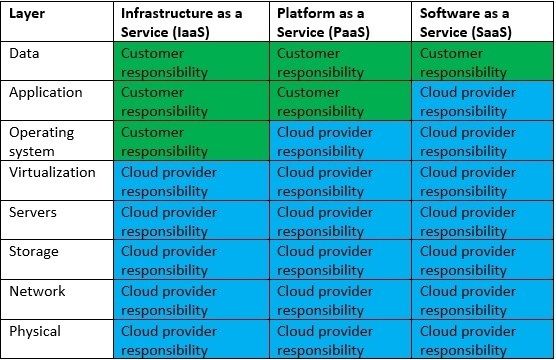
In the public cloud, we find a similar concept when talking about the shared responsibility model, where we draw the line of responsibility between the public cloud provider and the customers, in the different cloud service models, usually in terms of security, as we can see in the diagram below:
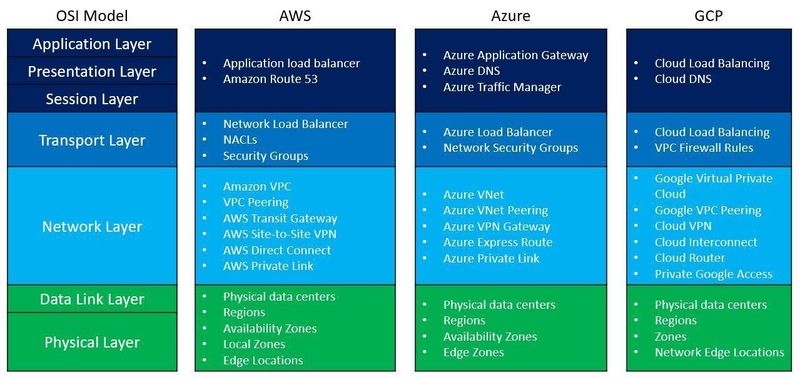
Where do public cloud services fit in the OSI model?
There are many networks related services in each of the major public cloud providers.
To make things easy to understand, I have prepared the following diagram, comparing common network-related services to the various OSI model layers:
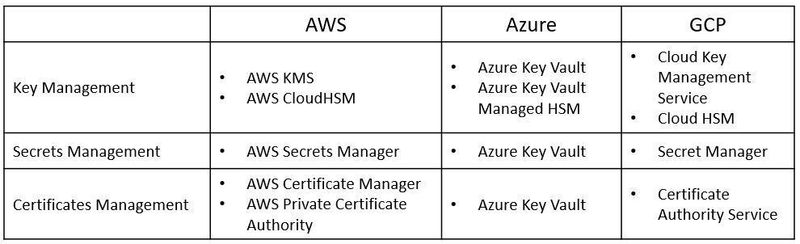
Encryption / Cryptography and the OSI Model
Layer 6 of the OSI model is the presentation layer.
Among the things, we can find in this layer is data encryption.
Encryption in this context is about encryption at rest – from object storage, block storage, file storage, and various data services.
Encryption includes symmetric and asymmetric encryption keys, secrets, passwords, API keys, certificates, etc.
The process includes the generation, storage, retrieval, and rotation of encryption keys.
Here are the most common encryption /cryptography-related services:
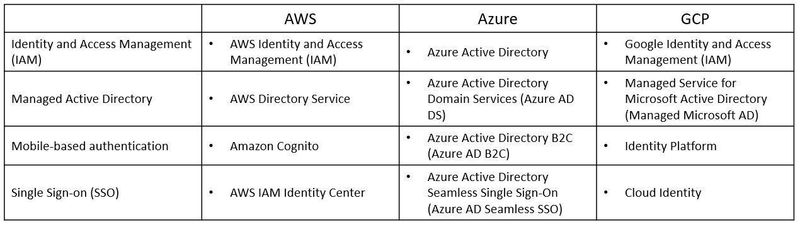
Identity Management and the OSI Model
Layer 7 of the OSI model is the application layer.
Among the things we can find in this layer are related to authentication and authorization, or the entire identity management.
Identity management is about managing the entire lifecycle of identity – from an end user, service account, computer accounts, etc.
The process includes account provisioning, password management (and MFA), permission management (role assignments), and finally account de-provisioning.
Here are the most common identity-related services:
How does everything come together?
When reviewing a cloud architecture, I like to compare the various services in the architecture to the different layers of the OSI model, from the bottom up:
- Network connectivity and traffic flow
- Encryption (according to data sensitivity)
- Authentication and Authorization (according to the least privilege principle)
The OSI model analogy, assist me to make sure I do not forget any important aspect when reviewing an architecture for a cloud workload.
About the Author
Eyal Estrin is a cloud and information security architect, the owner of the blog Security & Cloud 24/7 and the author of the book Cloud Security Handbook, with more than 20 years in the IT industry.
You can connect with him on Twitter and LinkedIn.


Top comments (0)