Security of the Cloud
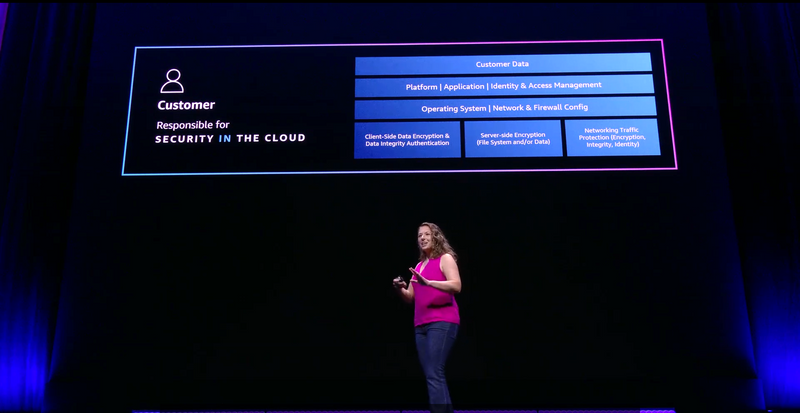
Security in the Cloud
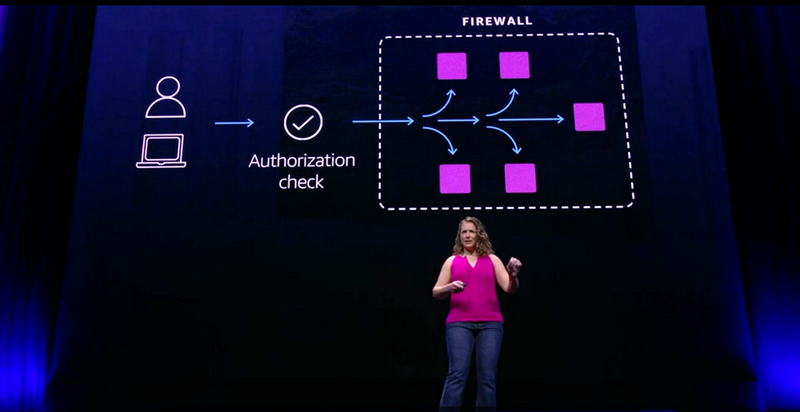
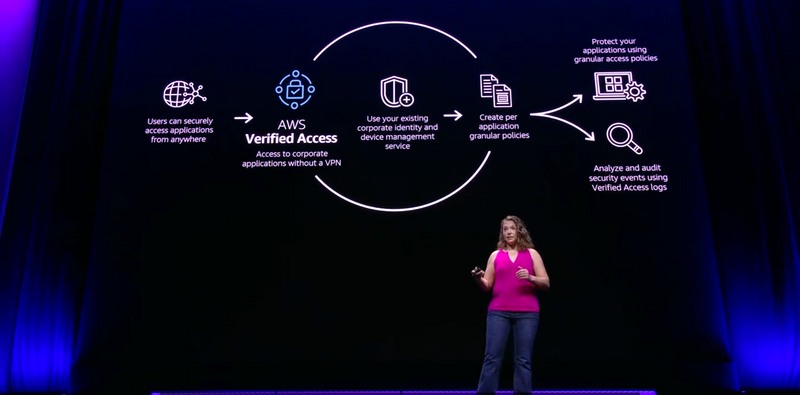
What are AWS Verified Access?
https://docs.aws.amazon.com/verified-access/latest/ug/what-is-verified-access.html
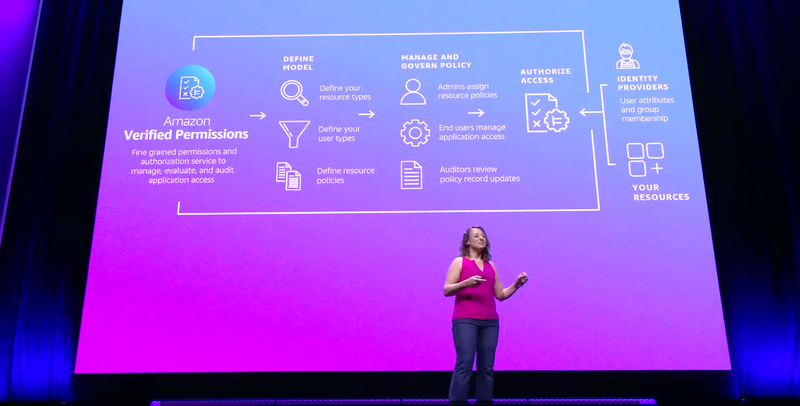
Announcement: AWS Verified Permissions
Purpose: Manage permissions and fine-grained authorization in applications that you build
References:
- https://aws.amazon.com/blogs/aws/simplify-how-you-manage-authorization-in-your-applications-with-amazon-verified-permissions-now-generally-available/
- https://aws.amazon.com/about-aws/whats-new/2023/06/amazon-verified-permissions-generally-available
- https://docs.aws.amazon.com/verifiedpermissions/latest/userguide/what-is-avp.html
Announcement: Amazon EC2 Instance Connect Endpoint
Purpose: Allows to connect to an instance via SSH or RDP without requiring the instance to have a public IPv4 address
References:
- https://aws.amazon.com/about-aws/whats-new/2023/06/amazon-ec2-instance-connect-ssh-rdp-public-ip-address/
- https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/Connect-using-EC2-Instance-Connect-Endpoint.html
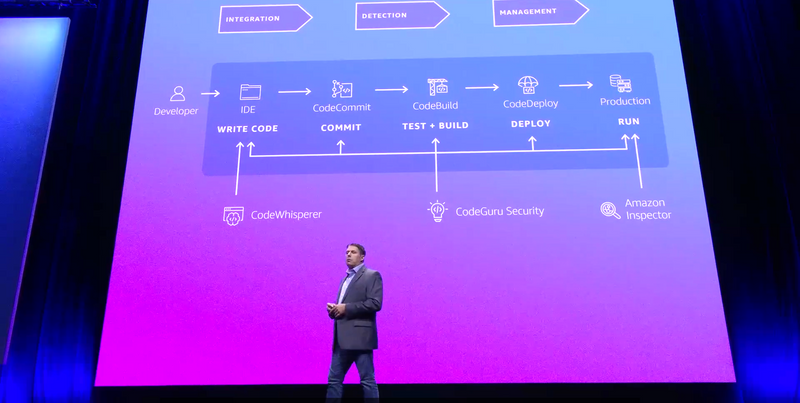
Announcement: Amazon Inspector Code Scan for Lambda
Purpose: Scans custom proprietary application code within a Lambda function for code security vulnerabilities such as injection flaws, data leaks, weak cryptography, or missing encryption based on AWS security best practices
References:
- https://aws.amazon.com/about-aws/whats-new/2023/06/amazon-inspector-code-scans-aws-lambda-function/
- https://docs.aws.amazon.com/inspector/latest/user/scanning-lambda.html
Announcement: Amazon Inspector SBOM Export
Purpose: Offers the ability to export a consolidated Software Bill of Materials (SBOMs) for all Amazon Inspector monitored resources across organization in industry standard formats
References:
- https://aws.amazon.com/about-aws/whats-new/2023/06/software-bill-materials-export-capability-amazon-inspector/
- https://docs.aws.amazon.com/inspector/latest/user/sbom-export.html
Announcement: Amazon CodeGuru Security
Purpose: A static application security testing (SAST) tool that uses Machine Learning to help identify code vulnerabilities and provide guidance to use as part of remediation
Note: This service is currently in preview
References:
- https://aws.amazon.com/about-aws/whats-new/2023/06/amazon-codeguru-security-available-preview/
- https://docs.aws.amazon.com/codeguru/latest/security-ug/what-is-codeguru-security.html
Announcement: Findings Groups for Amazon Detective
Purpose: Amazon Detective has expanded finding groups to include Amazon Inspector network reachability and software vulnerability findings alongside Amazon GuardDuty findings
References:
- https://aws.amazon.com/about-aws/whats-new/2023/06/amazon-detective-finding-groups-amazon-inspector/
- https://docs.aws.amazon.com/detective/latest/userguide/groups-about.html
About the Author
Eyal Estrin is a cloud and information security architect, the owner of the blog Security & Cloud 24/7 and the author of the book Cloud Security Handbook, with more than 20 years in the IT industry.
You can connect with him on Twitter and LinkedIn.


















Top comments (1)
The AWS re:Inforce 2023 keynote shared exciting updates on cloud security. It focused on new tools to keep data safe and help businesses stay protected. Great to see how technology is improving security for everyone!