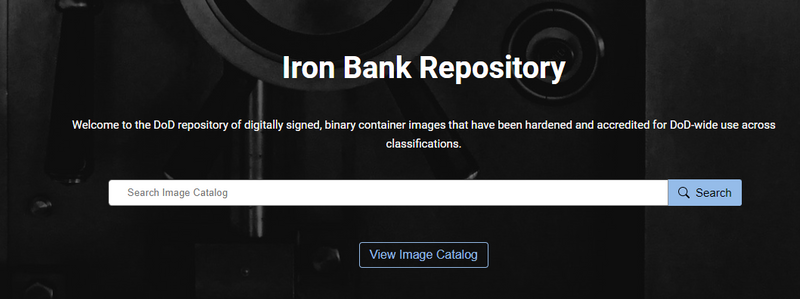
Iron Bank – DoD Centralized Artifacts Repository (DCAR)
Long story short...Iron Bank Centralized Artifacts Repository is a trusted repository management system to store U.S. Department of Defense artifacts. All artifacts stored in Iron Bank are hardened according to the Container Hardening Guide. DoD containers are OCI compliant and also have DoD-wide reciprocity across classifications.
Some of the main points that reduce the container's attack surface:
- Image building must start with a trusted image with known content from a trusted source.
- Use distroless images (which contain only application and its runtime dependencies, and don't include package managers/shells or any other programs you would expect to find in a standard Linux distribution). All distroless images are signed by cosign.
- The container image must be built with a non-privileged user in the build file.
Without further ado, let's give it a try. Platform one provides two front-ends when it comes to user experience:
1) Iron Bank DCAR
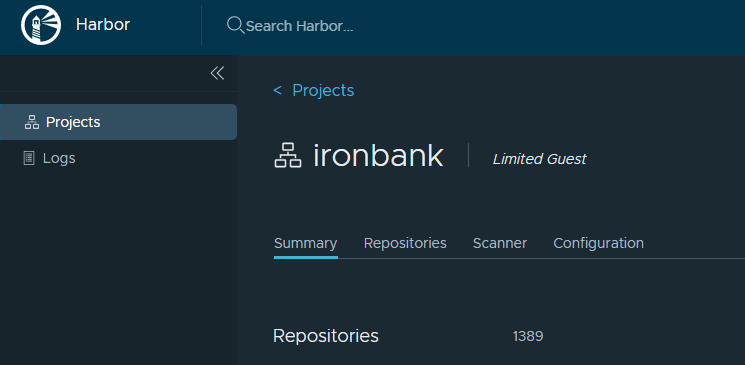
2) Harbor instance registry
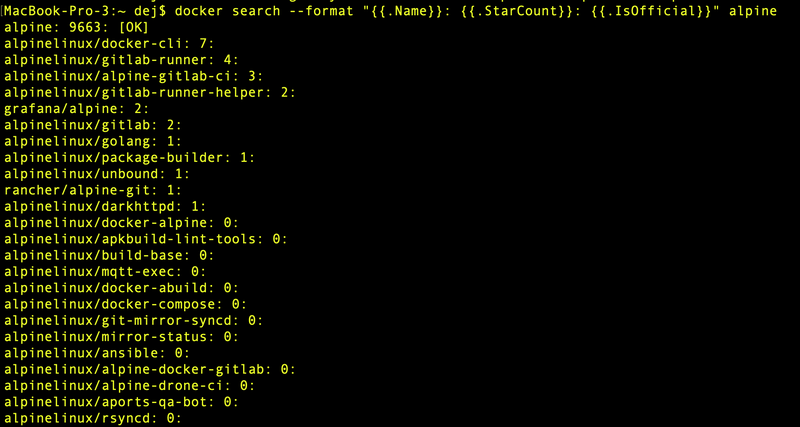
One of the most used base images is Alpine Linux (a security-oriented, lightweight Linux distribution),which is a "security-oriented, lightweight Linux distribution based on musl libc and busybox". Next I'll search for the official image:
docker search --format "{{.Name}}: {{.StarCount}}: {{.IsOfficial}}" alpine
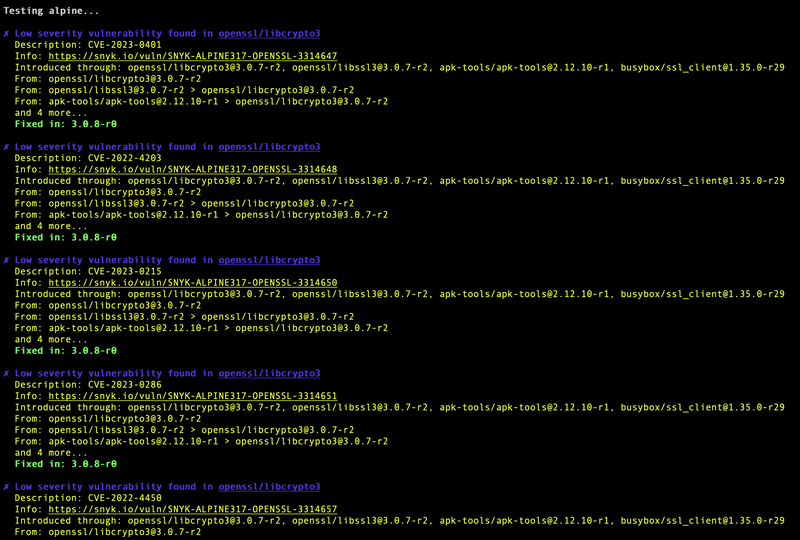
The Docker Official Images are a curated set of Docker repositories hosted on Docker Hub. I'm going to use Snyk to scan the alpine image.
The scan found 18 issues most of which are Low severity vulnerabilities.
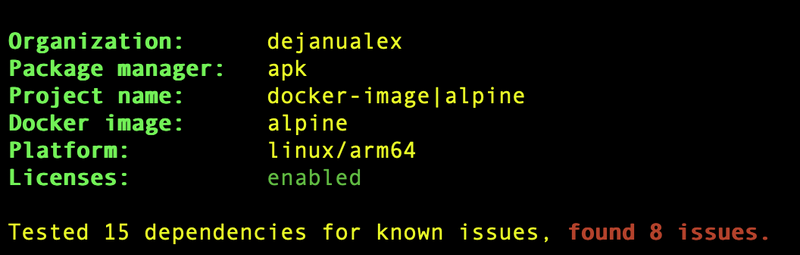
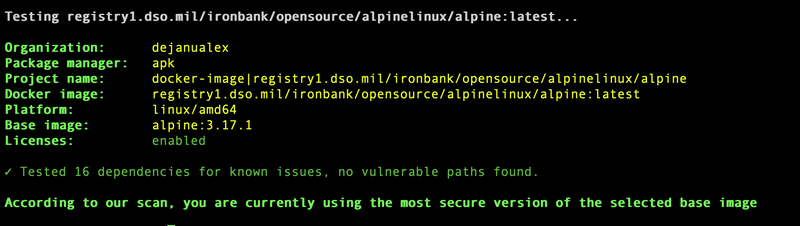
Now I'll scan ironbank's alpine image, and the result of the scan showed that accordingly to Snky's vulnerability database:
you are currently using the most secure version of the selected base image
In conclusion I highly recommend Iron Bank container registry since is one of the central registries used by the U.S. Department of Defense, and is maintained by the Platform One team.




Top comments (0)