IOCs, or Indicators of Compromise, are pieces of information that can be used to detect malicious activity on a network or system. By using a threat intelligence tool like VirusTotal, organizations can get more information about IOCs like the type of threat detected, its origin, or even which antivirus engines are detecting it.
In this guide, we'll show you how to use VirusTotal to verify an IOC and incorporate its results into an automated incident response workflow.
Verifying IOCs Using VirusTotal
When endpoint detection tools like CrowdStrike or SentinelOne detect malware, they will alert organizations and the incident will list IOCs. IOCs include such data as the IP address or domain name of a suspicious website, hashes associated with malware, and various other details related to an attack.
Using VirusTotal on a Browser:
If you are a SOC analyst and you want to know more information about the malicious website or software, you can go to the VirusTotal website. VirusTotal is a free service offered by Google which allows users to upload files, enter URLs, search IP addresses or file hashes, and scan these against the platform's antivirus databases.
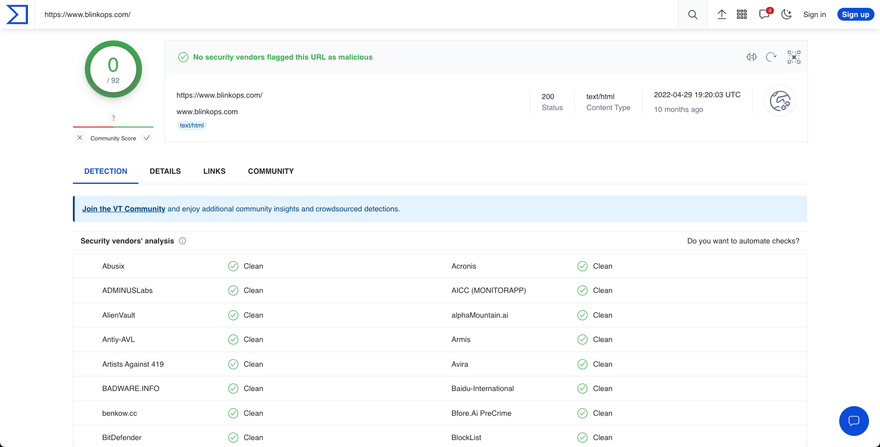
Here’s an example of what you would see if you submitted a file hash value that isn’t malicious:
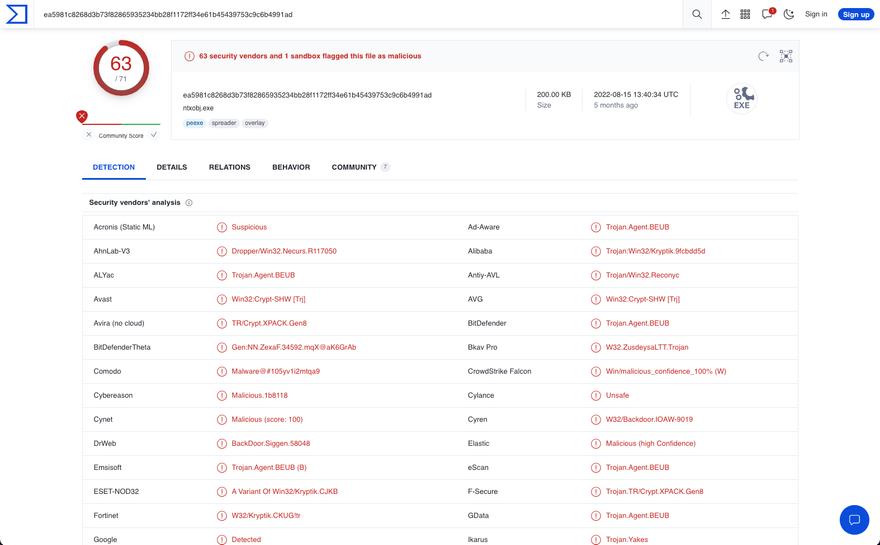
If you have a malicious file hash, you’ll see this information:
You’ll be able to view details like creation time, when it was first submitted, and when it was last analyzed, how it behaves, community comments, and more.
Using the VirusTotal API:
The VirusTotal API allows users to integrate their own custom scripts into the platform, enabling more advanced incident response workflows. For example, a script can be used to automatically upload suspicious files for scanning against the platform's databases.
To access the VirusTotal API, you’ll need to create an account and then you’ll have a free public API key you can use.
You can use this endpoint to get a file report:
curl --request GET \
--url https://www.virustotal.com/api/v3/files/{id} \
--header 'x-apikey: <your-API-key>'
You can use this endpoint to get a URL analysis report:
curl --request GET \
--url https://www.virustotal.com/api/v3/urls/{id} \
--header 'x-apikey: <your-API-key>'
And you can use this endpoint to get an IP address report:
curl --request GET \
--url https://www.virustotal.com/api/v3/ip_addresses/{ip} \
--header 'x-apikey: <your-API-key>'
If you review the API documentation, you may see other popular endpoints that better map to your incident & response process.
In the context of responding to an alert, you could save yourself a step by setting up a script to automatically call these endpoints with each respective piece of information and enrich your alerts.
Taking Action Based on VirusTotal Reports with Blink
When you enrich alerts with VirusTotal reports, you can save you time manually reviewing each detail. Instead of stopping at enrichment, what if you could utilize the results to kick off conditional responses?
For example, if an IOC is verified and has a high threat score, should you:
Immediately contain that device using your endpoint detection tool?
Search other devices across your organization to see if that IOC is present?
Add the IOC to your firewall and EDR blocking rules?
These might be the right steps, but if you scripted them all, you might not be able to control your automations easily at each stage.
With Blink, you can build event-based automations to facilitate incident response with conditional workflows and approval steps along the way. When a new alert is raised in an EDR like CrowdStrike or SentinelOne, you could immediately enrich that alert with reports from VirusTotal on each IOC.
Depending on the threat level, you can speed up your time-to-action with conditional response steps to fully leverage the combined power of the security and communication tools you’re already using.
You can start building a better response process with this pre-built Blink automation that verifies IOCs with VirusTotal. We have over 5K ready-to-use automations just like it in our library. By combining and customizing them, you’ll be able to create the workflows that match each security situation.
Get started with a free trial of Blink today or schedule time to see a demo.



Latest comments (0)