When malware is detected on one of your organization’s devices, it will have characteristics called Indicators of Compromise (IOCs), such as certain hash values, urls, or IP addresses.
You can use these IOCs to look across your organization’s devices to identify lateral movement associated with an attack.
In this guide, we’ll show you how to use CrowdStrike to detect if IOCs associated with malware are present on any other devices at your organization.
Searching for an IOC Across CrowdStrike Hosts
You can search for IOCs on other devices either by using the CrowdStrike Console or by using the CrowdStrike API.
Using the CrowdStrike Console:
1: First log in to the CrowdStrike Falcon Console.
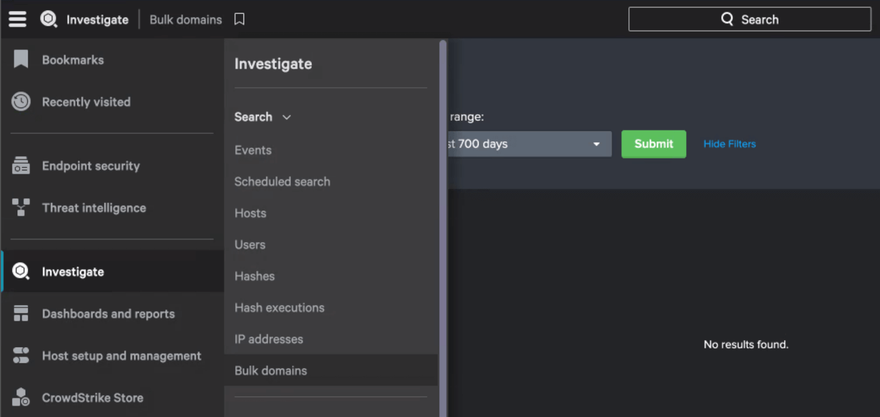
2: Open the left-hand menu and select Investigate.
3: Depending on your IOC type, choose the related link under the Search section. For example, if you are looking for an IOC that is a domain, you can choose Bulk domains.
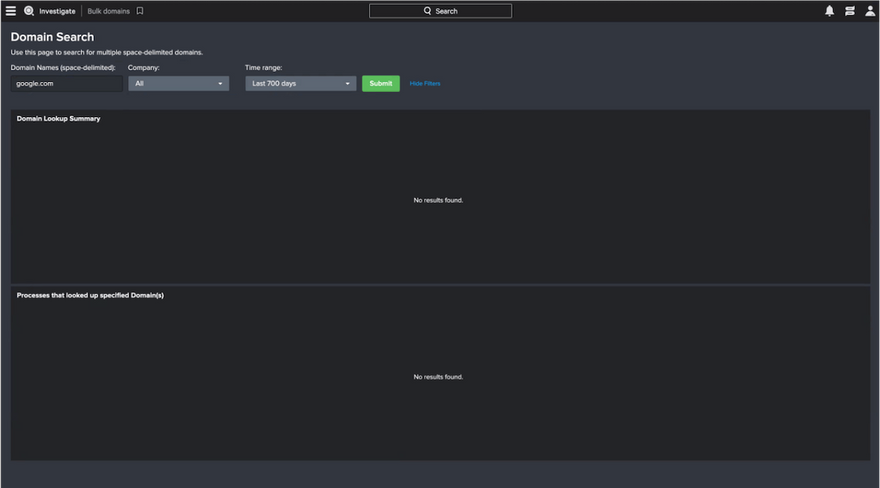
4: Input your IOC value and specify the time range you care about. Then click Submit.
In the results, you’ll see which hosts have observed the IOCs you’re investigating and you’ll see details on the process-level as well.
You may want to contain any additional hosts now associated with the IOC. We wrote a guide on containing hosts here. For your audit trail, you can export this data by hovering over either section and clicking the Export icon.
Using the CrowdStrike Falcon API:
The platform also offers an API which allows administrators to easily programmatically manage their sensors. You can use the endpoint that geographically aligns with your specific CrowdStrike account:
- US-1 “api.crowdstrike.com”
- US-2 “api.us-2.crowdstrike.com”
- US-GOV-1 “api.laggar.gcw.crowdstrike.com”
- EU-1 “api.eu-1.crowdstrike.com”
In the examples we show later, we’ll use “api.us-2.crowdstrike.com”.
CrowdStrike’s API documentation is available after you log in here, and you’ll see information about how to use OAuth2 for authenticating your requests.
Before you start, you need to make an access token request, including your client ID and client secret. You’ll get an access token in response that will be valid for 30 minutes after that. The API calls you make after that initial call will include that token.
Next, make a GET request to this endpoint with IOC type and value specified:
https://api.us-2.crowdstrike.com/indicators/queries/devices/v1?type=sha256&value=XYZ
You can use the following IOC types:
- sha256
- md5
- domain
- ipv4
- ipv6
You can also use the parameters limit and offset to manage pagination of results. With the response, you’ll be able to see all the resources that have observed the specific IOC.
Automatically Searching Across Devices for IOCs with Blink:
Checking if similar IOCs exist on other devices at your organization is one of many steps in responding to a security alert. While it isn’t difficult to do, it takes time and context-switching.
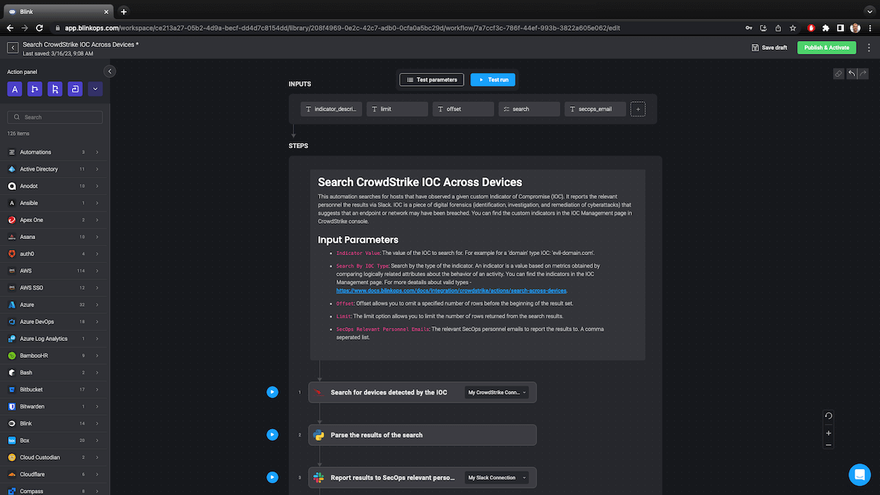
With Blink, you can handle this task automatically by just inputting an IOC type and value.
With these IOC inputs, this automation runs the following steps:
- Searches for other devices that have observed the IOC.
- Parses the results to format them into an easily readable report.
- Sends the report to the relevant SecOps team member via Slack.
This is a simple automation, and that makes it easy to customize. For example, you can add this as a subflow in larger incident response automation triggered by a CrowdStrike alert.
You can also use any of the 5K automations in the Blink library, or build new ones from scratch to fit your unique needs. In Blink, there are hundreds of native integrations and thousands of actions available to make building easy.
Start a free trial of Blink today to see how easy automation can be.



Oldest comments (0)