Resources in AWS should only be accessible to users who require them to complete tasks. If this principle of least privilege isn't followed, you increase the risk for data leakages or unauthorized access.
If you have EC2 AMIs that are publicly-shared for example, they are available to any AWS account and may contain sensitive data about your organization such as passwords, SSH keys, and configuration details.
In this guide, we will explain how to find and restrict publicly-shared AWS EC2 AMIs so you can ensure that sensitive information about your applications is not exposed.
Understanding AMIs for AWS EC2
An Amazon Machine Image (AMIs) is an image that enables you to easily launch Amazon Elastic Compute Cloud (EC2) instances with the necessary requirements preconfigured.
Each AMI includes instructions for block device mapping, launch permissions, and a root device volume, either backed by the EC2 instance store or at least one Amazon Elastic Block Store (EBS) snapshot.
You can use an AMI to launch single instances or multiple servers in a cluster. For example, if you are launching a web server that handles a large volume of traffic, you can use an AMI to deploy it quickly. You can also launch multiple instances in the same cluster and configure them to work together.
These AMIs can be shared with specific users, giving them access to the same configurations and settings. If they are publicly-shared, AMIs can reveal sensitive information about how your instances function.
How To Find Any Public AMIs in AWS
Since AWS EC2 AMIs are publicly shared by default, it's easy to miss if you haven't taken the time to check your settings. Luckily, there are two ways to check whether your AMIs are publicly shared. You can use the Amazon EC2 Console or the AWS CLI, depending on your AWS environment.
Using the AWS Console:
This method is the most straightforward way to check if your AMIs are publicly shared. Follow these steps:
- Log in to the AWS Management Console.
- Select EC2 from the list of services.
- Click AMIs in the left sidebar menu under the IMAGES section.
- To see all the public AMIs, use the first filter in the AMI list and choose Public Images.
- To check individual AMIs, select one and scroll down to the Permissions section and check the current permissions. If the selected AMI is publicly shared, the EC2 dashboard will display the following message, "This image is currently Public" in the Permissions section.
Using the AWS CLI:
You can also use the AWS Command Line Interface (CLI) to check whether your AMIs are publicly shared. This process is a bit more complex, but here's how it works:
- Run the following describe-images command:
aws ec2 describe-images --executable-users all
The command will return a list of all the publicly shared AMIs in your account. If the command returns images with the Public parameter value of "true" then the AMI is publicly accessible.
For instance, the AMI in question is publicly shared if the output is something like this:
{"Images": {"ImageId": "ami-1234abcd", "Public": true } }
Now that you have identified public AMIs, next you can update them to make them more secure.
Changing Public AMIs to Private AMIs in AWS
You can update public AMIs to restrict access using either the AWS Console and CLI.
Using the AWS Console:
- Log in to the AWS Management Console again and select EC2 from the services list.
- Select the AMI you want to make private from the list of AMIs in the IMAGES section.
- Head to the Permissions tab from the bottom bar menu on your dashboard. Click on Edit AMI Permissions.
- Then select Private and Save changes to make the AMI private. The Permissions tab will now display the following message, "This AMI is not shared with any other accounts."
Using the AWS CLI:
- Run the following modify-image-attribute command to make an AMI private:
aws ec2 modify-image-attribute
--image-id ami-1234abcd
--launch-permission "{\"Remove\":[{\"Group\":\"all\"}]}"
This will immediately make the AMI private while preserving all its existing permissions.
To double-check, you can list the attributes of the image by running the following describe-images command for the AMI with the id “ami-1234abcd”:
aws ec2 describe-images --image-ids ami-1234abcd
The output should now display the Public parameter as false as shown here:
{"Images": { "ImageId": "ami-1234abcd", "Public": false}}.
Now, you have successfully secured your non-compliant AMI.
Automating AWS Permission Checks for EC2 AMIs with Blink
It isn’t hard to find and secure public AMIs, but it can be time-consuming if you have many that need to be addressed or you want to check this on a regular basis.
How do you ensure that you don’t have overly-permissive AMIs at any given time? If you are only doing this task with CLI commands or steps in the console, you will need to context-switch to oversee each step.
With an automation platform like Blink, you can run this automation to identify and notify your team of new public AMIs so you can maintain consistent compliance.
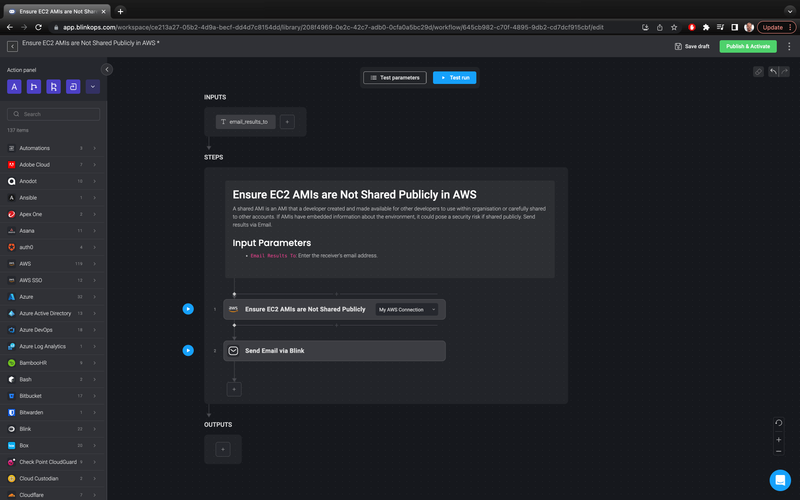
This automation in the Blink library executes the following steps:
- Checks if there are any publicly-shared AWS EC2 AMIs.
- Sends a report to a specified email address.
This is a simple automation, which makes it easy to customize for your organization’s needs. For example, you can add actions to update the settings of non-compliant AMIs with just an approval via Slack.
This automation and 5K more are available for you to use right away from the Blink library. Instead of manually implementing best practices with the AWS console or CLI, these ready-to-use automations enable you to set and enforce policies across your organization or teams.
You can also build custom automations to match your organization’s unique use cases, whether you want to schedule a task, run steps based on an event in a certain tool, or share a self-service application for your coworkers to use.
Start a free trial of Blink today or schedule time with us to see more.



Top comments (0)