Azure Arc is a management tool that allows you to extend Azure management features to resources not hosted within Azure. A key feature of Azure Arc-enabled servers is the ability to use virtual machine (VM) extensions to enhance server functionality. These extensions, analogous to those available for Azure VMs, offer capabilities such as monitoring, patch management, and script execution. In this blog post, we will explore the basics of Azure Arc VM extensions and provide detailed guidance on how to manage them, including how to allow or block specific extensions for enhanced security and control.
What are VM Extensions for Azure Arc-Enabled Servers?
VM extensions are add-ons that can be deployed on Azure Arc-enabled servers to provide additional functionality. These extensions are developed by Microsoft and select third parties and are stored in Microsoft-managed storage accounts. They are identical to extensions available for Azure VMs, ensuring consistency across different environments.
How Extensions Work
Extensions are downloaded from Azure Storage at the time of installation or upgrade unless private endpoints are configured, in which case extensions are proxied through regional URLs. A digitally signed catalogue file verifies the integrity of each extension package, ensuring that only trusted extensions are executed.
Configuring Extension Settings
Extensions can accept settings to customise their behaviour, such as proxy URLs or API keys. These settings can be classified into regular settings and protected settings. Protected settings are encrypted at rest on the local machine and are not persisted in Azure.
Monitoring and Control via Azure
All extension operations are initiated from Azure through API calls, CLI commands, PowerShell scripts, or portal actions. This design ensures comprehensive logging of all actions in the Azure Activity Log. Although extensions can be removed locally for troubleshooting, they will be reinstalled during the next sync if the service still expects them to be present.
Security Controls: Allowlists and Blocklists
Starting with agent version 1.16, Azure Arc allows you to control which extensions can be installed on your servers using allowlists and blocklists:
- Allowlists : Only the specified extensions can be installed. This is the most secure option as it blocks any new or unauthorised extensions by default.
- Blocklists : Any extension except those specified can be installed.
Configuring an Allowlist
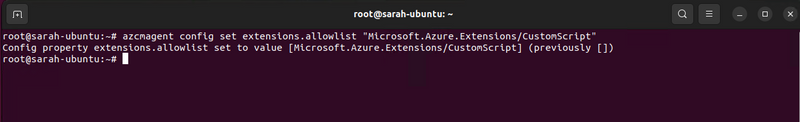
To allow only specific extensions, such as allowing the custom script extension to be allowed on your Linux server you can use the command:
azcmagent config set extensions.allowlist “Microsoft.Azure.Extensions/CustomScript”
Configure Azure Arc agent extensions in Linux
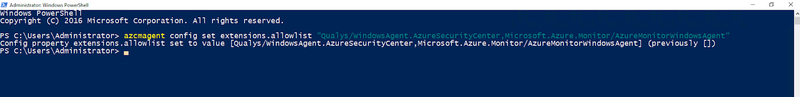
You don’t have to do each extension individually you can do multiple extensions at once. For example, if you want to allow the Microsoft for Defender extension and the Azure Monitor Agent on your Windows server you can use the command:
azcmagent config set extensions.allowlist “Qualys/WindowsAgent.AzureSecurityCenter,Microsoft.Azure.Monitor/AzureMonitorWindowsAgent”
Configure Azure Arc agent extensions in Windows
Configuring a Blocklist
To block the extension for the Log Analytics agent you can run this command on your Windows machine:
azcmagent config set extensions.blocklist “Microsoft.EnterpriseCloud.Monitoring/MicrosoftMonitorAgent”
This is a command block that I see customers putting in place as The Log Analytics agent, also known as the Microsoft Monitoring Agent (MMA), is retiring in August 2024.
You can find a full list of extensions available either on Windows or Linux on the official documentation page: https://learn.microsoft.com/azure/azure-arc/servers/manage-vm-extensions#extensions
Add an extension to an existing allow or block list
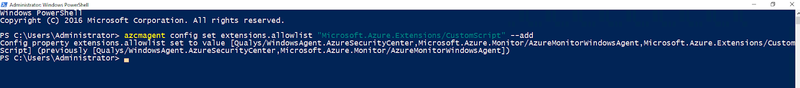
If you have an existing allow or block list configured you may need an additional flag to add the extension. For example, if you want to add the Custom Script to an existing allow list you would append the ‘--add’ flag to the command, see below:
azcmagent config set extensions.allowlist “Microsoft.Azure.Extensions/CustomScript” --add
Configure Azure Arc agent extensions in Windows
Remove an extension to an existing allow or block list
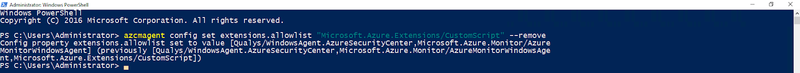
If you have an existing allow or block list configured you may need an additional flag to remove an additional extension. For example, if you want to remove the Custom Script to an existing allow list you would append the ‘--remove’ flag to the command, see below:
azcmagent config set extensions.allowlist “Microsoft.Azure.Extensions/CustomScript” --remove
Configure Azure Arc agent extensions in Windows
Azure Arc-enabled server extension Security Practices
For enhanced security, especially on sensitive servers like Active Directory Domain Controllers or servers handling payment data, you can use additional measures:
Use allowlists instead of blocklists whenever possible to block unauthorised extensions by default.
Disable Guest Configuration to prevent custom policies from changing the agent configuration.
Avoid including the Custom Script Extension in your allowlist to prevent the execution of potentially harmful scripts.
Using Agent Modes
Agent modes simplify the configuration process for common scenarios:
- Full Mode : Default mode allows all agent functionalities.
- Monitor Mode : Restricts functionalities to monitoring and security-related extensions only.
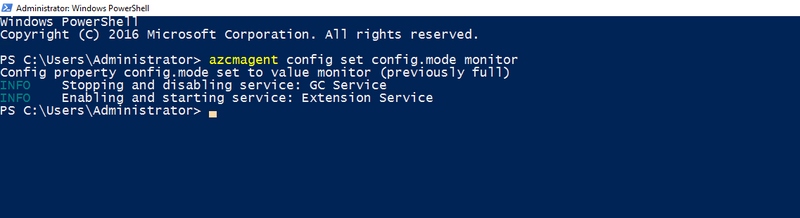
To enable monitor mode, use the following command:
azcmagent config set config.mode monitor
Configure Azure Arc agent extensions in Windows
As new extensions become available that enable monitoring scenarios, Microsoft will update the allowlist and agent configuration to include or exclude the new functionality, as appropriate.
Disabling the Extension Manager
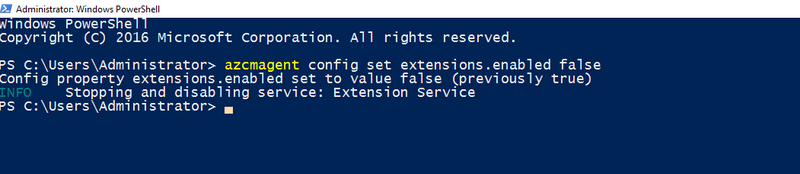
If you do not need any extensions, you can disable the extension manager entirely:
azcmagent config set extensions.enabled false
Configure Azure Arc agent extensions in Windows
This step ensures that no extensions run on the server.
Check the current status of extensions
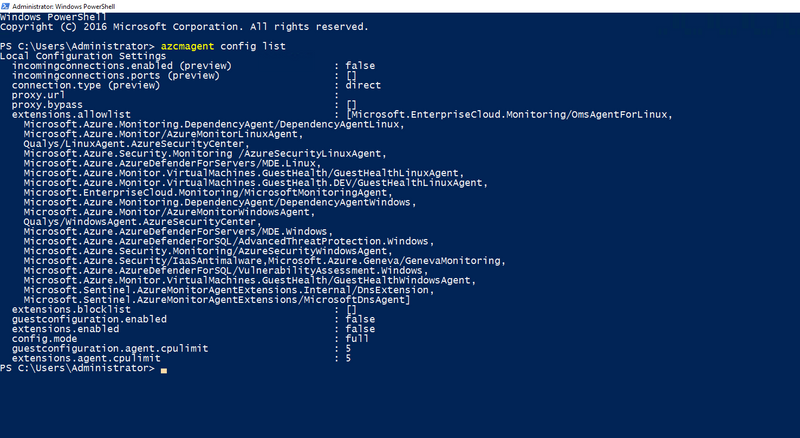
You can check the current mode of the agent and understand what extensions are allowed or blocked you can use the following command:
azcmagent config list
Configure Azure Arc agent extensions in Windows
Conclusion
Azure Arc VM extensions offer powerful capabilities to enhance server management and functionality. By configuring allowlists and blocklists, you can maintain tight control over which extensions are installed, ensuring your servers remain secure and compliant with organisational policies. With the flexibility of Azure Arc, you can tailor the server management experience to fit your unique needs, whether for monitoring, security, or specific operational requirements.



Top comments (0)