What is secret management?
Secret management is the process of securely storing and managing sensitive information such as keys, passwords, and tokens. Secrets are used to provide privileged access and are usually stored in secure environments using secret management tools.
Hard coding secrets or insecurely sharing them can lead to vulnerabilities both in terms of external attacks and internal mishandling. Practicing secret management becomes even more crucial as your team, request load, and cloud services scale. It is a deal breaker for any organization that wants to be compliant with privacy and security standards such as PCI DSS, HIPAA, and GDPR.
Some of the most common types of secrets include:
- Account credentials
- Database credentials
- Passwords
- Certificates
- SSH keys
- API keys
- Encryption keys
Increasing threats
In this blog, we will focus on the different types of secret management tools, how they differ, and what are some things to look for while evaluating such tools. With more companies adopting modern infra practices, You will find many up-and-coming solutions part of this list. In fact, the secret management space is in its growth trajectory with a lot of VC funding into companies like Doppler, which raised $20M, and Akeyless, which raised $65M. Grandview research predicts that the secret management market alone will be worth $2.05 Billion by 2025.
This increased funding correlates with the increased threat of exposed secrets. Companies, on average, lose $1.2 Million in revenue per year due to leaked infrastructure secrets. GitGuardian reported having detected over 6M secrets in public Git repositories in 2021. Furthermore, managing secrets is tedious and costs the company. DevOps and IT engineers spend an average of 25 minutes per day managing secrets; that’s an annual payroll expense of roughly $8.5 billion.
With secret management being such a widespread issue impacting users, employees, and revenue, it is important to take the time to include a secret management tool in your stack.
This blog is part one of a three part series covering secret management. In future posts we will cover kubernetes native tools and have an in-depth comparison.
We classify Secret management tools into three categories based on who built the tool.
- Cloud Service Provider (CSP) tools
- Platform agnostic tools
- Open Source tools
CSP secret management tools
Cloud service provider tools are tools built by cloud providers such as Azure, AWS, Google Cloud, Oracle, IBM, and Alibaba cloud. This list focuses only on AWS, Azure, and GCP tools. While using CSP tools, it is important to note that they function well with other services from the same provider but do not have a good experience or may not work with third-party tools and services.
AWS
AWS has over 25 products in its Cloud security, identity, and compliance services offering, making it one of the most mature offerings. Here, we primarily look at the tools that directly deal with cloud secrets.
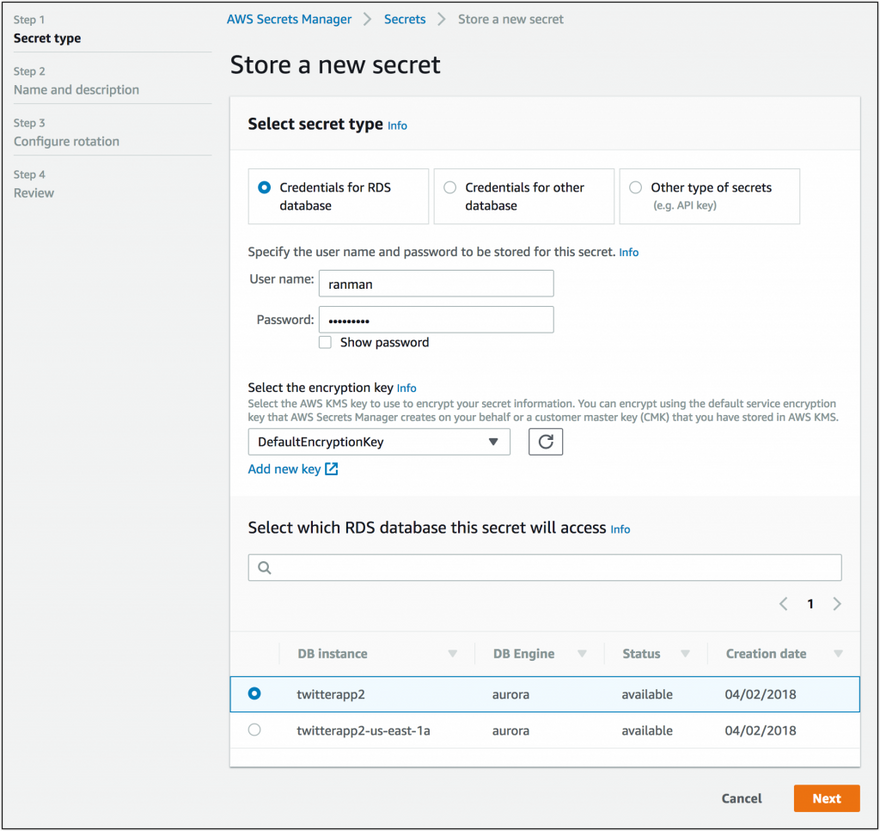
Image source: https://aws.amazon.com/blogs/aws/aws-secrets-manager-store-distribute-and-rotate-credentials-securely/
AWS Secrets Manager
The AWS Secrets Manager is the centralized store for all your AWS secrets, from API keys to DB credentials and tokens. It can be a secret for your application, services, and also IT resources. Its ability to manage the lifecycle of secrets and its integration with other AWS services enables automated monitoring. Works in hand with IAM and helps meet all security and compliance requirements. It comes with a 30-day free trial, followed by $0.40 per secret per month & $0.05 per 10,000 API calls.AWS Parameter store
AWS Parameter store is a secure store for configuration data and secrets. It is a part of AWS Systems Manager and is used to store and retrieve parameters, which are key-value pairs. AWS Systems Manager provides a centralized store to manage your configuration data, whether plain-text data such as database strings or secrets such as passwords. This has the huge advantage of being tightly integrated with other AWS services like AWS KMS and IAM.Amazon Macie
Amazon Macie is a data security and privacy service that automatically uses AI and ML to look in S3 for sensitive data by pattern matching. It maintains a growing list of sensitive data types, including personally identifiable information (PII) and other sensitive data types defined by data privacy regulations, such as GDPR, PCIDSS, and HIPAA. Start with a 30-day free trial.AWS Key Management Service (KMS)
AWS’s KMS tool helps users create, control, and manage keys to encrypt or digitally sign their data. It works across all your applications deployed using AWS and with more than 100 AWS services. KMS requests are also recorded in a log file if you’re using AWS CloudTrail. The system is also designed to be scalable, durable, and highly available. AWS Free Tier includes 20,000 free AWS KMS requests each month.AWS Certificate Manager (ACM)
AWS Certificate Manager is an easy way to purchase, manage, and deploy public and private SSL and TLS certificates for use with AWS services and your internally connected resources. Certificates can be created through the ACM console or call to ACM’s API. It can also automatically renew in-use and DNS-validated ACM-issued certificates. Public SSL/TLS certificates can also be provisioned through AWS Certificate Manager for free.
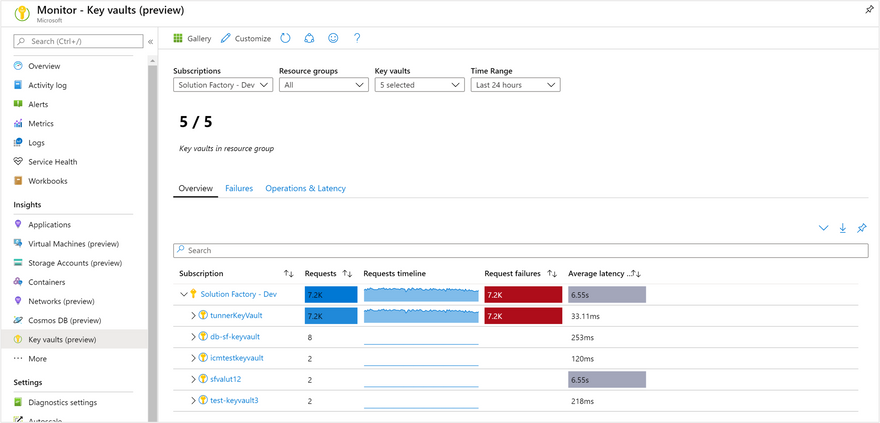
Azure Key Vault
Azure Key Vault helps increase control and security over keys. It allows creating and importing of encryption keys in just minutes. Automated key rotation is also available. It simplifies and automates tasks for SSL/TSL certificates. It also provides managed HSM pools for storing and managing HSM-backed cryptographic keys. You can create a free account and get 10,000 transactions of RSA 2048-bit keys or secret operations for Key Vault free, full pricing details can be found here.
Image source: https://learn.microsoft.com/en-us/azure/key-vault/key-vault-insights-overview
Google Cloud
Google Cloud brings strong cloud security and threat protection suite of services with its vast AI-backed protection and the recent acquisition of Mandiant. They offer over 20 security and identity management products, many with automation features and high scalability.
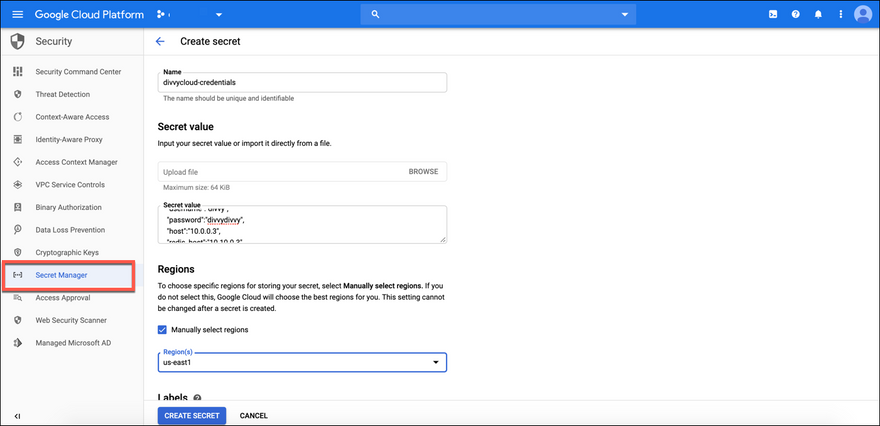
Image source: https://docs.divvycloud.com/docs/gcp-secrets-manager
Google Secrets Manager
It is a single place to store all API keys, passwords, certificates, and other sensitive data. Easy to follow the Principle of Least Privilege with IAM roles and grant individual permissions to secrets. Other features like automated rotations using cloud functions and secret life cycle management are also available. There’s also an open-source command line tool Berglas that’s available for accessing and managing these through CLI. The secret manager pricing can be found here.Cloud Key management
Google Cloud's key management tool is a service that allows users to manage and store their encryption keys securely. The tool provides a centralized and easy-to-use platform for managing keys during storage and transit. It helps users to comply with security and regulatory standards and is integrated with other Google Cloud services. The tool allows users to easily manage and rotate their keys regularly, reducing the risk of keys being compromised. It is a comprehensive solution for managing keys across different teams and applications. Pricing information here.
Platform agnostic tools
Platform-agnostic secret management tools allow users to securely manage and store sensitive information such as passwords, encryption keys, and other confidential data. They are designed to be flexible and adaptable so that they can be used on a wide range of different platforms.
This means that users can use the same tool on different systems, across their multiple cloud services, OSes, and platforms like mobile, without having to worry about compatibility issues. They are often used in conjunction with other security tools and protocols to provide a comprehensive solution for protecting sensitive data.
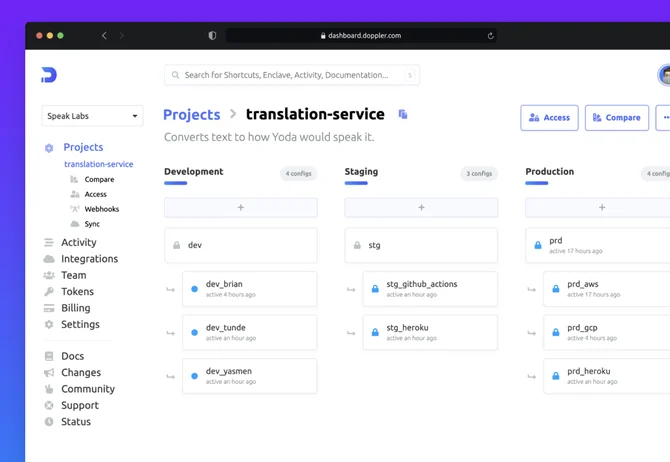
Doppler
Appealing to a wide range of customers, from startups to enterprises, is Doppler. Doppler’s SecretOps platform is a central hub for all your team’s and cloud’s secrets. It can be accessed through the dashboard, API, and CLI and can manage secrets across cloud providers, deployment pipelines, users, local machines, and more.
Doppler allows easy collaboration with your team with a single source of truth that is encrypted and organized across projects and environments. Its automation features let you create references to frequently used secrets in Doppler. When they need to change, you only need to update them once.
Image source: https://github.com/marketplace/doppler-secrets-manager
Versioning comes as part of the package, with an option to add slack alerts and easy rollbacks through API and CLI. Check out all the integrations available here. There is a forever free plan for up to 5 users, and paid plans to include developer, team, and enterprise plans starting at $7/mo/additional user.
Hashicorp Vault
Hashicorp Vault is a popular open-source secret management tool developed by HashiCorp that tool allows users to securely store, manage, and access sensitive information such as encryption keys, passwords, and other confidential data.
One of the key features of Hashicorp Vault is that it provides a centralized and easy-to-use platform for managing secrets. This allows users to manage all of their secrets in one place, which can be particularly useful for organizations that need to manage large amounts of sensitive data.
Hashicorp Vault also provides a range of advanced features for securing secrets. For example, the tool allows users to easily generate and rotate encryption keys, which can help to reduce the risk of keys being compromised. It also provides support for multiple authentication methods, including support for two-factor authentication, which can help to protect against unauthorized access.
Image source: https://www.hashicorp.com/resources/vault-oss-ui-introduction
It is also highly scalable and can be used in a wide range of different scenarios. The tool can be deployed on-premises, in the cloud, or in hybrid environments and can be easily integrated with other cloud provider tools and services.
The self-managed version of Hashicorp Vault is available for free, and the managed cloud version comes with additional features like fully managed clusters and Cloud SLA and starts at $0.03/hr. There’s also an enterprise version available with premium support, governance, and policy.
AKeyless Vault platform
AKeyless is a unified, SaaS-based vault platform to create, store, and secure credentials, certificates, and keys across hybrid multi-cloud environments. Being a SaaS solution, it offers broad functionality and ease of use while also being fast to production and comes with OOTB connectors to migrate your existing secrets.
Maintenance of the platform is also quite easy, and it scales for peak demand across your regions and cloud platforms. Their innovative and patented Distributed Fragments Cryptography (DFC technology) is what’s behind the AKeyless Vault platform and it enables Zero-Knowledge Encryption for secure DevOps and Cloud transformations.
Image source: https://faun.pub/akeyless-vault-review-intuitive-secrets-management-solution-for-your-devops-workflow-c867bd298608
Their secret management features are available starting at free for smaller teams with five clients with up to 2,000 static secrets and team plan starts at $15/client/month. The secure remote access is available with a 30-day free trial and then charged monthly beyond that.
1Password
1Password is a password management tool developed by the company AgileBits. The tool allows users to securely store and manage their passwords and other sensitive information such as app credentials, SSH keys, credit card numbers, and account details. 1Password has a wide range of customers, from families to businesses to developers, and is available on a range of platforms, including Windows, Mac, Linux, iOS, and Android.
The 1Password Connect Server is a self-hosted secrets server that comes with a Secrets Automation workflow, using which you can securely access your 1Password items and vaults in your company's apps and cloud infrastructure using a private REST API.
Its ability to seamlessly integrate with the development workflow right from the command line and VS code integrations makes it a tool of choice for developers. Using this tool, you can also manage SSH keys and Git more securely. You can easily integrate with other services like Terraform and also your Kubernetes clusters.
Image source: https://developer.1password.com/docs/cli/verify/
The pricing information can be found here; there’s also a free trial of 14 days and it comes with 50% off your first year.
Delinea
Delinea has a suite of products around privilege access management and security. The product not only monitors and records privileged sessions but can also alert and help control unauthorized access. The tools work smoothly across on-prem and cloud platforms. The two products DevOps Secrets Vault and Secret server, provide coverage for most secret types, from application secrets to database credentials to CI/CD tools.
It has industry-leading features like Just-in-time database access, X.509, and SSH certificate issuing, with automatic signing and distribution. Easy and automated scaling and more. They have good free resources to help you access your requirements. Their pricing isn’t available publicly and they seem to be more suited to enterprise customer needs. You can request a quote to know more about their offerings and pricing.
Image source: https://delinea.com/products/secret-server
Onboardbase
Onboardbase is a tool built with cloud-native solutions and remote devs in mind. The tool offers great collaboration capabilities with teams and contractors. It also enables the creation, sharing, and cloning of configurations for easier collaboration and onboarding. End-to-end encryption, exposed vulnerability detection, and device management make the tool suitable for enterprise needs as well. Here is the list of frameworks supported and integrations available. The pricing can be found here. There is a free plan for small teams of up to 3 users.
Image source: https://onboardbase.com/blog/linux-environment-variables
Keeper
Keeper has three tools related to security. A password manager, a secret manager, and a connection manager for remote access. Keeper Secrets Manager is a fully managed, cloud-based, zero-knowledge platform for securing infrastructure secrets such as API keys, database passwords, access keys, certificates, and any type of confidential data.
With options like a browser extension, and a mobile app, your secrets are always accessible to you. Its backend also comes with High Availability built-in and it also works offline. Vault secrets can be accessed through an intuitive UI or by using the CLI. There are several integrations available to connect with your favorite cloud tools and many developer SDKs are provided to let you manage and update secrets.
They have several pricing options that support teams of all sizes. Further, they have student and military discounts with an additional 20% off on annual plans.
Image source: https://www.keepersecurity.com/blog/2020/05/29/protect-more-than-just-your-passwords-with-keeper-secure-file-storage/
BeyondTrust
BeyondTrust has a DevOps secrets management tool that protects secrets used by apps and other non-human identities in the CI/CD toolchain. This is one of the several tools they have for securing privileged access to your apps and infra resources.
The tool is built around productivity by taking a REST API-first approach and the CLI tool provides your teams with a preferred UX that helps drive fast adoption. It also has tools for managing remote access and Endpoint privilege management on Windows, Mac, and Linux. Though they claim their pricing to be transparent, it is not available publicly on their website.
Image source: https://www.beyondtrust.com/
Knox-app
Knox is a Secret as a Service platform to improve dev team security by managing secrets, keys, and configurations securely. Knox works with any CI, server, Dev environment, or platform that can make an HTTPS request. Built around simplicity, the tool offers all features with ease of use in mind.
From AWS secrets to public google analytics keys across environments can all be brought to one secure storage. The ability to grant access using tokens and easily update secrets are other useful features of this tool. Their free tier works for 1 project, and paid tier starts at just $2/mo. They also have an enterprise option at $50/mo.
Image source: knox-app.com/
More Open Source Tools
These open source tools secret management tools are developed in a collaborative manner, with contributions from a wide range of individuals and organizations. These tools were primarily built by independent companies and are now being actively maintained by the community.
The significance of open-source secret management tools lies in their transparency and accessibility. Because the source code is freely available, users can easily inspect the inner workings of the tool and verify that it is secure and free from vulnerabilities. This can help to build trust and confidence in the tool, and can also encourage collaboration and innovation within the community.
Another key advantage of open-source secret management tools is that they are often more flexible and customizable than commercial tools. Because users have access to the source code, they can modify the tool to meet their specific needs and requirements or integrate it with other tools and services. Few of these tools offer enterprise versions for those interested.
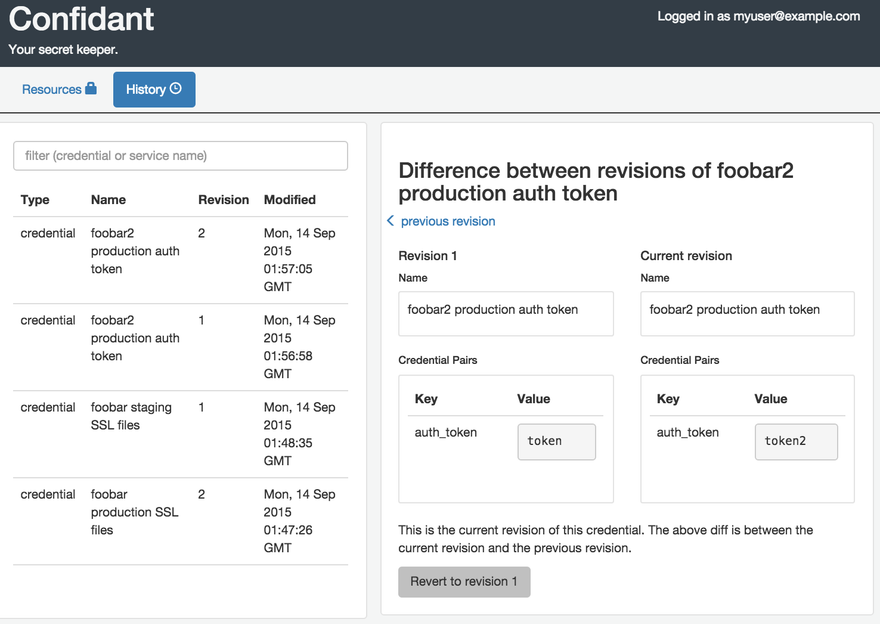
Confidant by Lyft
Confidant is a simple-to-use tool for AWS secret management with two underlying concepts: secrets and the mappings of those secrets to services. Both secrets and their mappings to services are revisioned, and no revision is ever deleted. The configuration can be done via Bash or in Docker format.
Secrets are encrypted and stored at rest in an append-only way in DynamoDB, generating a unique KMS data key for every revision of every secret, using Fernet symmetric authenticated cryptography. Confidant has two views: the resources view and the history view.
Image source: https://lyft.github.io/confidant/using_confidant.html
Envkey (YC W18)
Envkey is the central place to manage all your app secrets, from development to CI to staging to production. It can work with any host, any language and also helps your team ship faster by preventing config bugs and keeping your environments in sync. You can connect to your server using Heroku, Docker, and Kubernetes. Their cryptography is based on NaCl and ed25519.
The Self-Hosted option runs in an AWS account you control. You can use it with any host or cloud provider. Setup takes less than an hour. Once deployed, it runs hands-free. Scaling, backups, and patches are all automatic. They also have various pricing plans to suit your needs.
Image source: https://docs-v2.envkey.com/docs/apps
Knox by Pinterest
Knox is a service to manage, keep track of and protect secrets that are used by other services, including cloud platforms, encryption keys, TLS certificates, and other third-party secrets. The main problem Knox aims to make it easier for developers to access and organize secrets, keep an audit log to understand who has accessed and has access to the keys, and provide mechanisms to rotate keys in case of compromise.
It is built using Go and is straightforward to set up using Docker. Knox consists of several parts. From the lowest level, Knox depends on another service (like MySQL) to store the data and provide methods for secure cryptography. Knox has a server component that can access this data store and cryptor. Knox also has a client layer that lives on machines across the fleet. This client layer caches keys on the local file system for use by services on those machines.
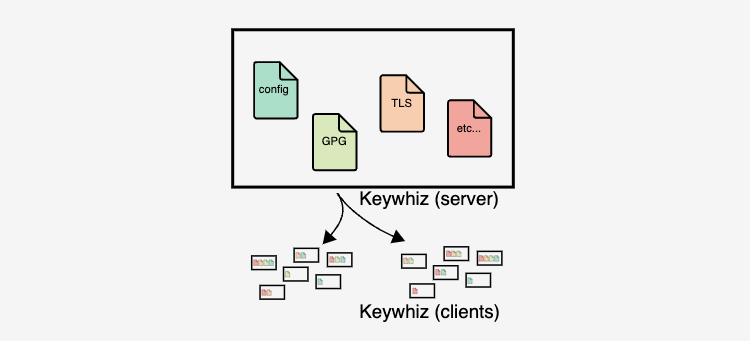
Keywhiz by Square
Keywhiz, an open-source project by Square, is used to manage secrets and ensure your sensitive files are always available on the right servers. It is most useful when your server and network infrastructure grow, and you need a solution that scales reliably. The secrets are encrypted during distribution and rest. Keywhiz implements fine-grained access controls to allow specific access to each application-host pair.
It can store any type of secret file, including application configurations, database credentials, GPG keys, TLS keys and certificates, API tokens, etc. It also supports Hardware Security Module (HSM).
Image source: https://square.github.io/keywhiz/presentation.html
Choosing a secret management tool
Okay, that’s a lot of secret management tools.
But how does one choose a tool for their secrets?
To do so, you should start by asking yourselves (& your team members involved in handling secrets) these questions:
- Where your current secrets are stored and managed?
- Who are the users of these secrets? Will they access the secrets using CLI/API/UI or a combination of these?
- Which secrets do you want to manage? App, infra, databases, IoT, containers, or others?
- Is your strategy to manage multi-cloud and multi-infrastructure tools secrets in one place?
- What policies should you enforce for your secrets? Versioning, revoking secrets, rotating secrets, time-based policies, back-up, resiliency, etc.
Once you answer these, you get a clearer understanding of your secret management requirements. You might want to look at additional considerations before landing on a tool.
- The size of your team, and how geographically distributed they are, importance of securing remote access.
- Whether you have a lot of contractors accessing secrets or it’s just internal team members.
- Understand if the tool provides RBAC or other types of access management to ensure safe keep of your secrets.
- Your current CI, Git, and DevOps tooling. Check out which tools have the integrations required with minimal change for you to start with. If your current stack is all over the place, that’s fine too. Check if it makes sense to bring all secrets into one place or take a more distributed strategy.
- Check for enterprise readiness and scalability of the tool. Always be prepared for 10x the volume of secrets you are currently handling. Hackers are always out there looking for sensitive information, especially at fast-growing companies like yours.
- For an open-source tool, estimate how much effort is needed to get it set up.
- Start with a tool that has a free tier and fits your current demand. Then choose tools with transparent pricing models to avoid any unexpected hikes in costs.
- Few tools can automatically look for secrets using pattern matching and ML models. These might be useful if you suspect your existing code base has exposed secrets and also if you have a lot of publicly accessible code.
- Check your comfort level with sticking to a cloud provider solution. It brings better integration, and familiar UX, but also leads to vendor lock-in.
While no one tool can meet all situations, your choice would ultimately come down to your app’s setup, infra requirements, and who needs access to these secrets. Secret management also encompasses data and application security; thus, thinking about risk management and having a solid secret management strategy can help you accelerate faster.
Now that you have a list of cool secret management tools to try out, it’s time to improve your secret management. Start by assessing your current state and requirement with the five questions mentioned above. Then use the additional considerations while narrowing down on your tool of choice.
Note: The secret management space is just beginning to bloom and there is room for several innovations to come. Thus, this list can only cover some of them.
Come back for part two where we cover native kubernetes secret management tools like sealed secrets and external secrets operator.
Argonaut has a native secret management solution for small teams. Argonaut integrations with third party secret providers is coming soon Q1CY23.
With Argonaut’s modern deployment platform, you can get up and running on AWS or GCP in minutes, not weeks. Our intuitive UI and quick integrations with GitHub, GitLab, AWS, and GCP make managing your infra and applications easy - all in one place.



Top comments (2)
This is a helpful post for anyone wanting to keep their cloud data safe. Free Spire Therapy can help you understand and accept this plan. It clearly explains different secret management tools and how to pick the best one. Easy to understand and useful for beginners too.
Hey, can we use secret management tools for automotive sites? Like, we sell utv cab enclosures so what you will recommend?